Threat modeling workflow for Microsoft Threat Modeling Tool
Threat modeling workflow for Microsoft Threat Modeling Tool
Prerequisites
You're expected to have followed the previous step by step tutorial (Threat modeling workflow for AWS Cloudformation architectures using IriusRisk) to configure the IriusRisk API and the Postman API client so that they can speak to each other in a seamless way.
You should use the latest version of the IriusRisk API documentation published at SwaggerHub.
Microsoft Threat Modeling Tool
The Microsoft Threat Modeling Tool (MTMT) is one of the longest lived threat modeling tools, having been introduced as Microsoft SDL in 2008, and is actively supported; version 7.3 was released in March 2020.
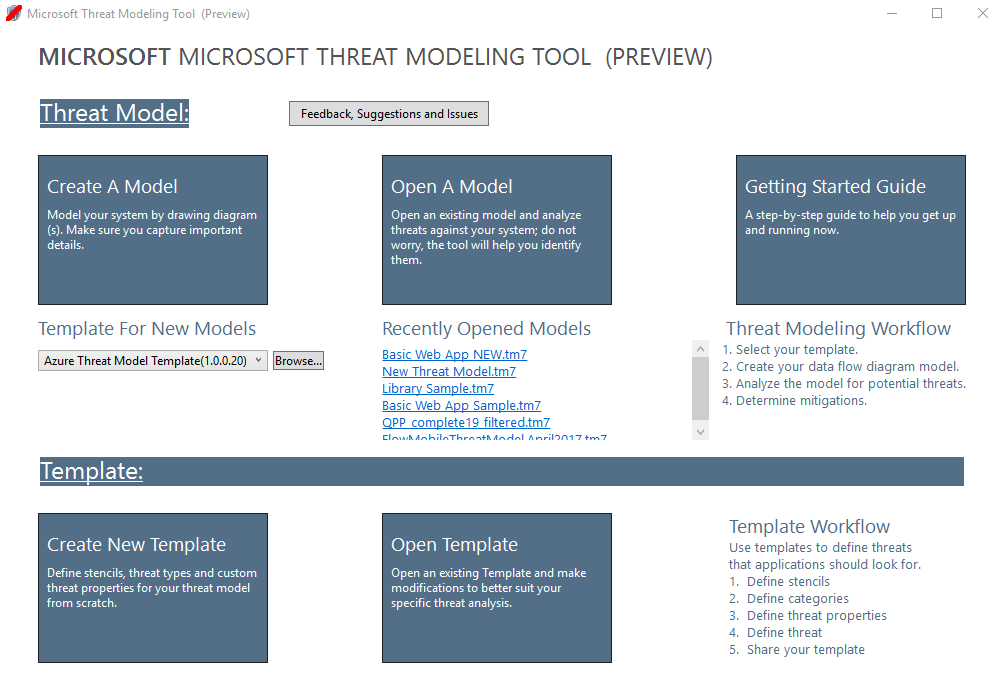
Nowadays, the Microsoft Threat Modeling Tool is a free click-to-download application for Windows.
Follow this step by step tutorial to import an architecture defined using MTMT in IriusRisk as a hands-on example. This feature is still in the early stages of development and doesn’t allow you to import the whole MTMT threat model yet, only the architecture. However, we’ll continue progressing in this direction in the following releases. You can find below an illustration of the architecture we’ll be using along with this article:
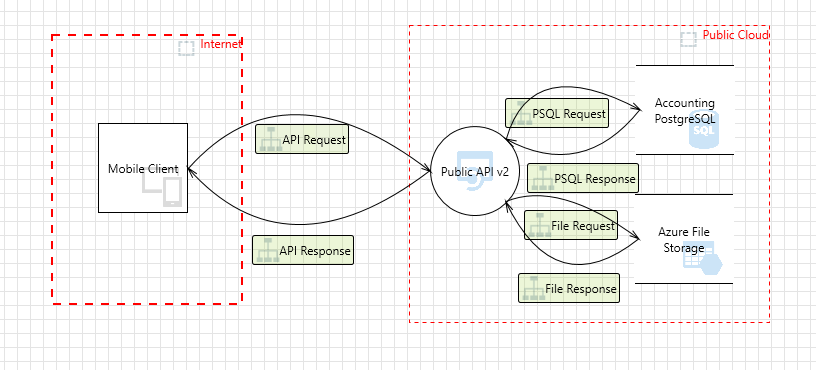
How to use Postman to automatically create a threat model in IriusRisk from an MTMT diagram
Now we can use Postman to upload this MTMT template to automatically create a new threat model in IriusRisk for this example architecture. In order to do this, you can follow the next three steps:
Step 1: Select the TMT API endpoint
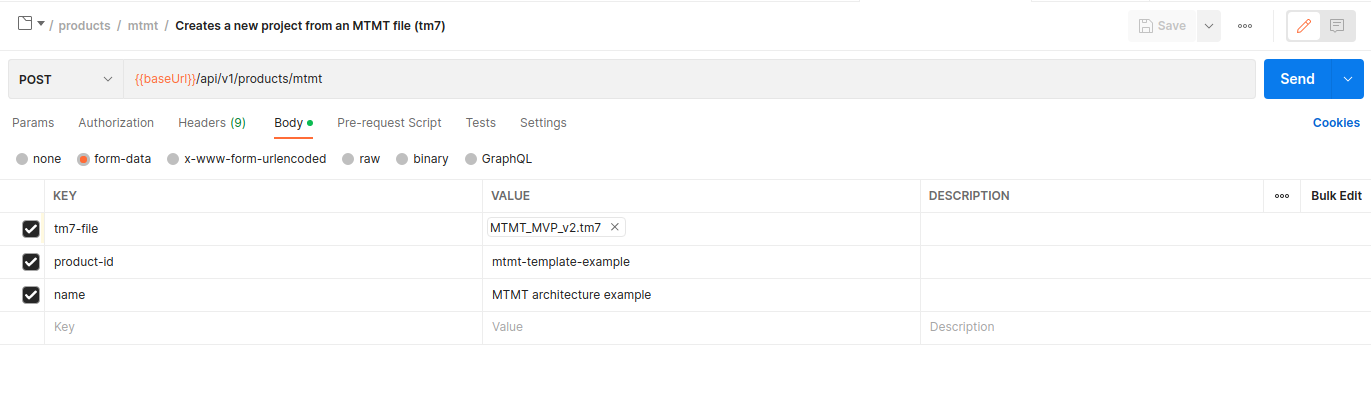
First, we need to use the MTMT endpoint (POST/api/v1/products/mtmt) in the Postman collection navigation tree. This API endpoint is intended to create a new IriusRisk project from an MTMT file (tm7).
Step 2: Set the API request parameters
Now, we'll set the HTTP body parameters:
- tm7-file: (Required) File that contains the MTMT file.
- product-id: (Required) Id of the new project in IriusRisk.
- name: (Required) Name of the new project in IriusRisk.
- mapping-file: (Optional) File that contains the mapping between generic MTMT shapes and IriusRisk components.
To keep this importation template simple, we'll use the default mapping between MTMT shapes and IriusRisk components. This way, we won't need to specify the mapping-file and we can deselect this parameter in the Postman checkbox. One example of the structure for this mapping file could be found in the StartLeft Github repository. Right now, this default mapping file supports some basic MTMT components. However, we’ll continue expanding this default mapping file in the next IriusRisk releases, but if you need to customize this mapping to fit your specific requirements, you’ll be able to provide your own YAML mapping file to the API using the mapping-file variable.
The next step, is to select our simple example for a MTMT defined architecture (MTMT_MVP_v2.tm7) as the value of the tm7-file parameter. Then we set the product-id and name parameters that will be used to create a new project in IriusRisk. Finally, we click on the "Save" button to persist this configuration. This is how it looks in the HTTP POST request configuration right now:
Step 3: Send the API request
We are ready to click on the "Send" button to actually send the HTTP request and create the new IriusRisk project from our MTMT template. If everything goes well, we'll receive a 201 HTTP code from the IriusRisk server and the following Body response with some basic information about the newly created project:
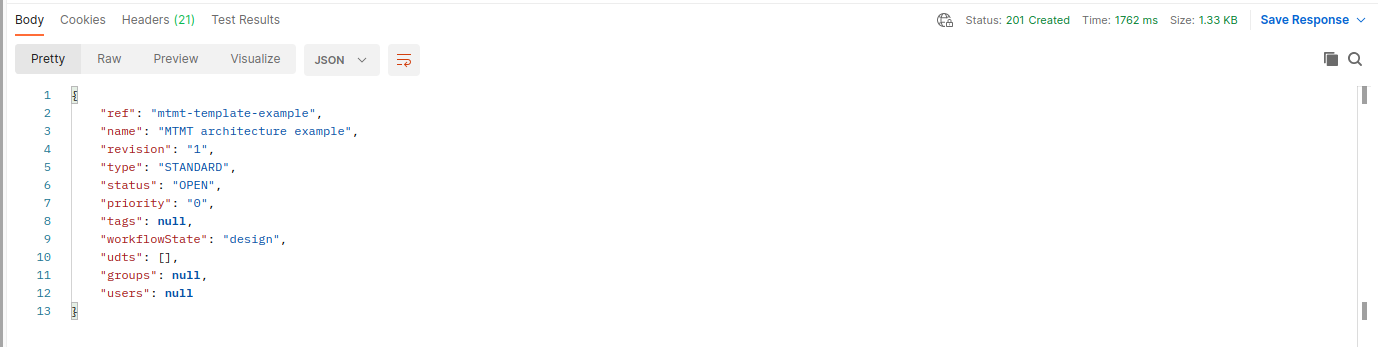
Review the generated threat model in IriusRisk
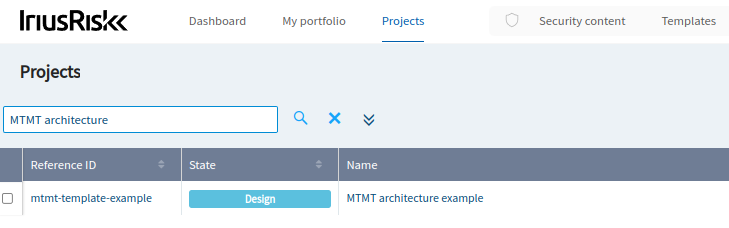
If we log in in the IriusRisk UI, we'll see that a new threat model was automatically created based on our MTMT template architecture:
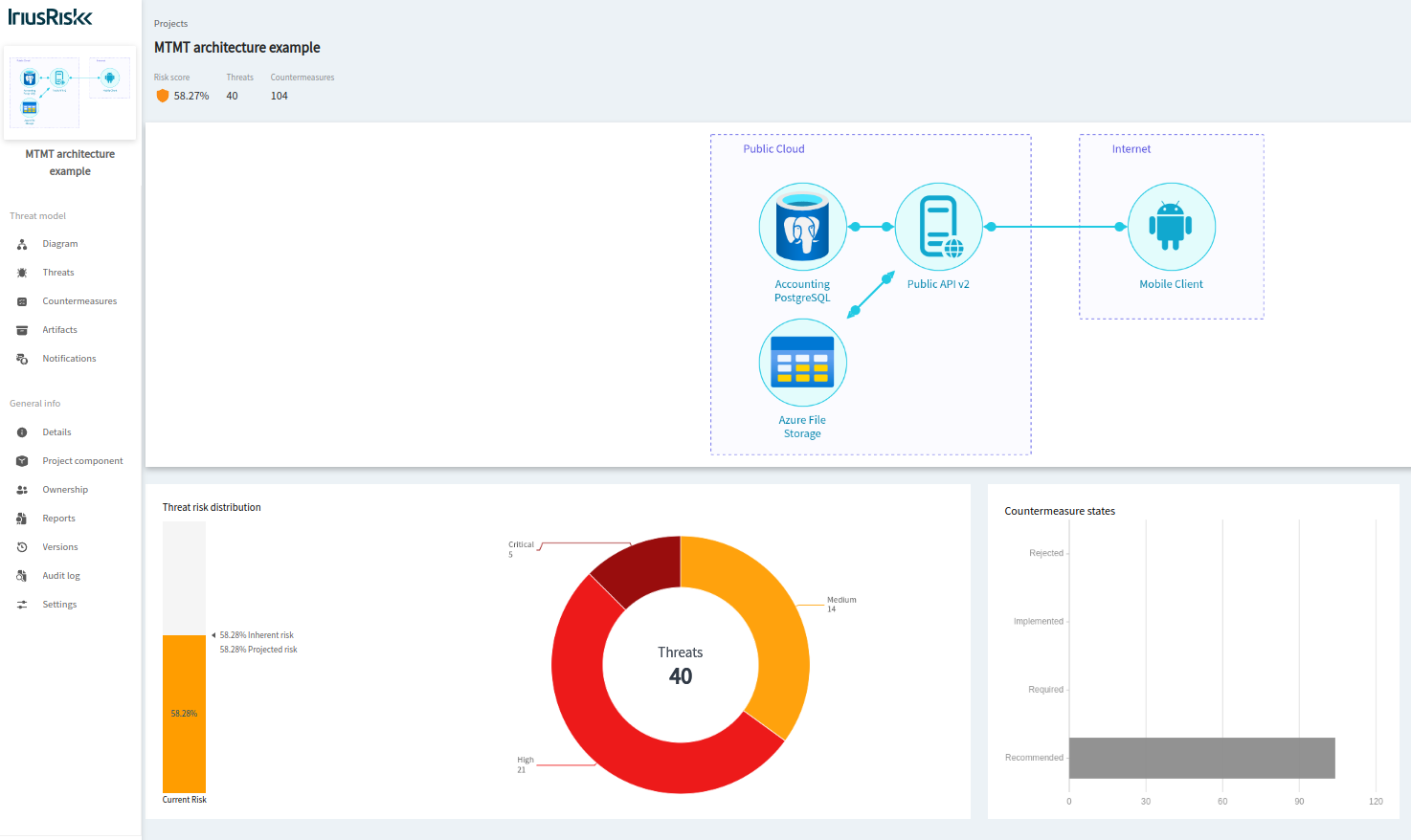
This is how it looks in the project home page as a visual summary of some of the main security metrics involved for this threat model:
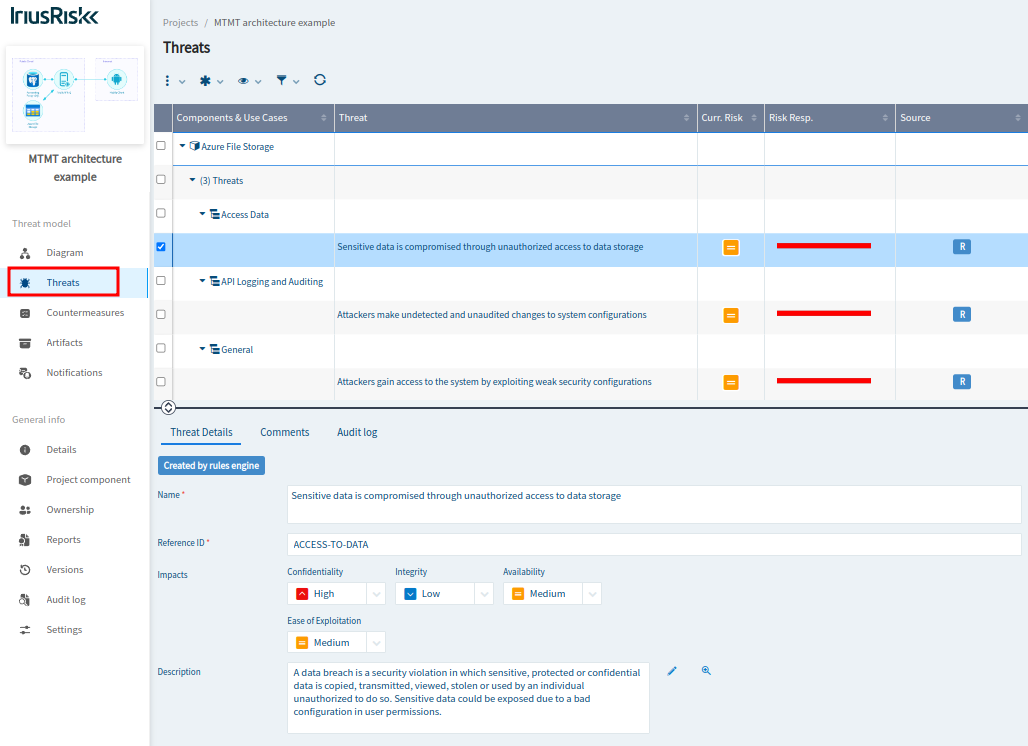
To see the relevant threats and countermeasures for this simple architecture, you can go to the "Threats" section on the left pane:
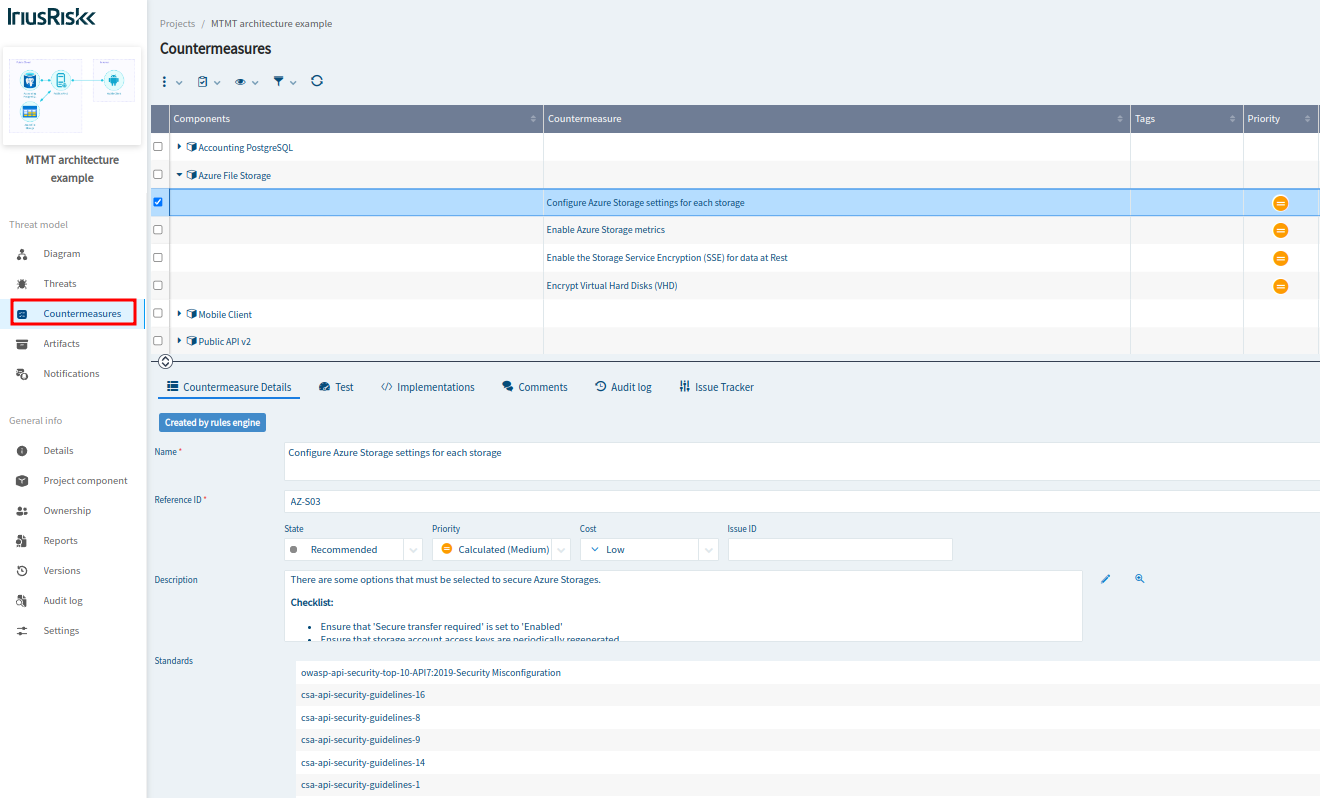
To take a look at the recommended countermeasures, you should visit the “Countermeasures” section:
Conclusion
In this step-by-step tutorial we've seen how to automatically create a threat model in IriusRisk from a simple architecture designed with Microsoft Threat Modeling Tool (MTMT).
References
- IriusRisk Release 4.9: https://www.iriusrisk.com/resources-blog /(future-entry-for-4.9)
- IriusRisk API Swaggerhub documentation: https://app.swaggerhub.com/apis/continuumsecurity/IriusRisk/
- IriusRisk StartLeft GitHub project: https://github.com/iriusrisk/startleft
- Microsoft Threat Modeling Tool: https://learn.microsoft.com/en-us/azure/security/develop/threat-modeling-tool-releases



