
Product Release 4.45 Featuring Image Upload to Jeff AI, Plus Improved Imports for Visio & Lucidchart
Overview
This release details new features and improvements, including improved imports for Visio and Lucidchart Diagrams, as well as the ability to use your images in Jeff AI! Take a look at the full information below, or go directly to the Release Notes here.
- Use your Images in Jeff AI to Generate Diagrams
- Improvements to Visio and Lucidchart Imports
- Bulk Permission Management for Business Units' Users
- Unanswered Questionnaires to Improve Threat Modeling Accuracy
Upload Your Images to Jeff AI to Generate Diagrams
Customers may have architecture diagrams in other platforms, and tools. Starting these complex diagrams again from scratch is not an option, especially with multiple applications, limited time, and resources. Now users can upload their images into Jeff AI, and witness it match the relevant components, before generating a full threat model.
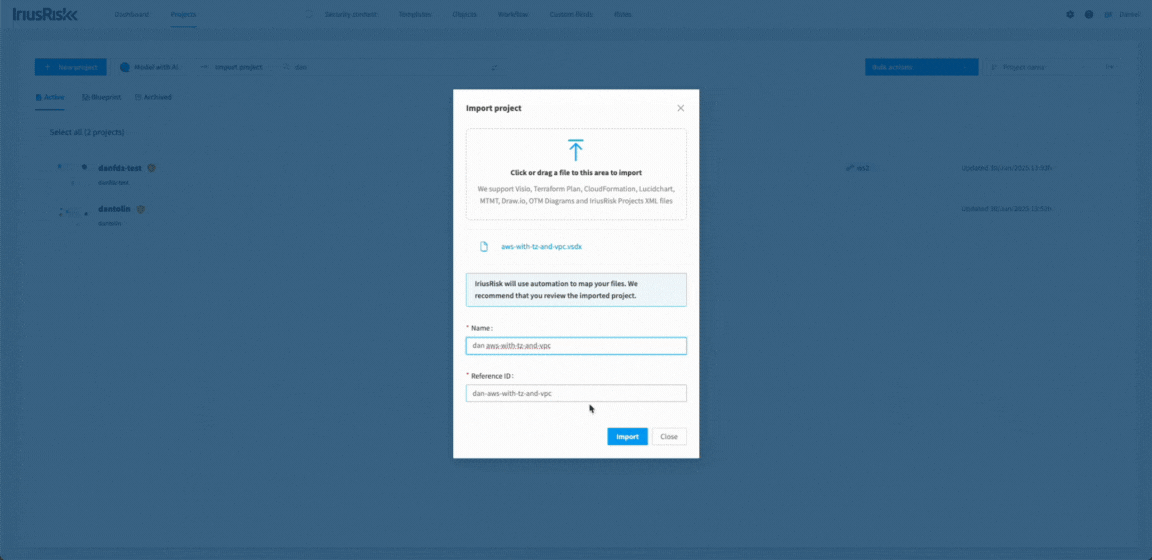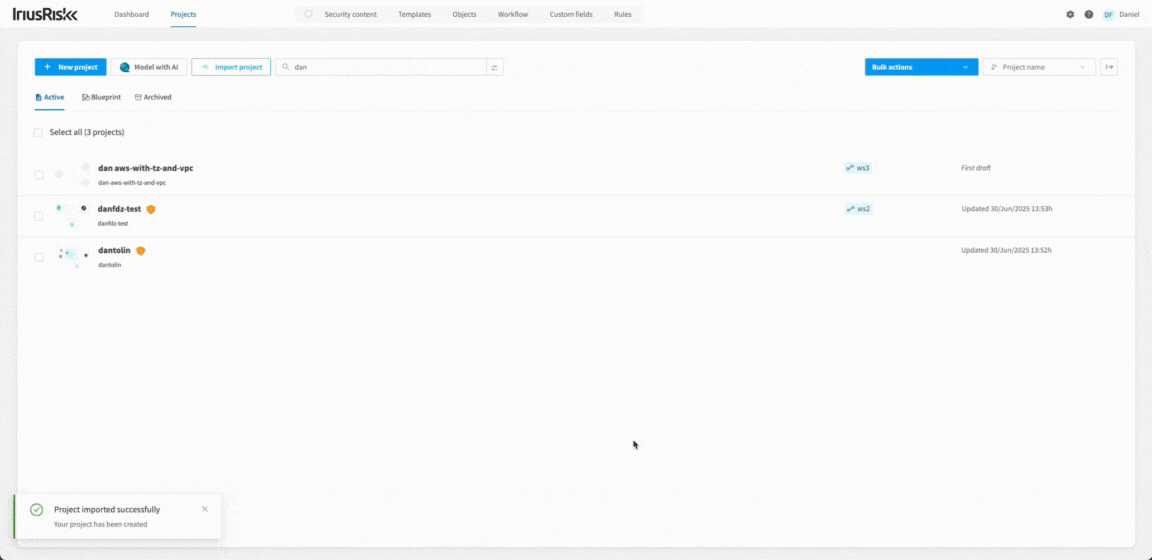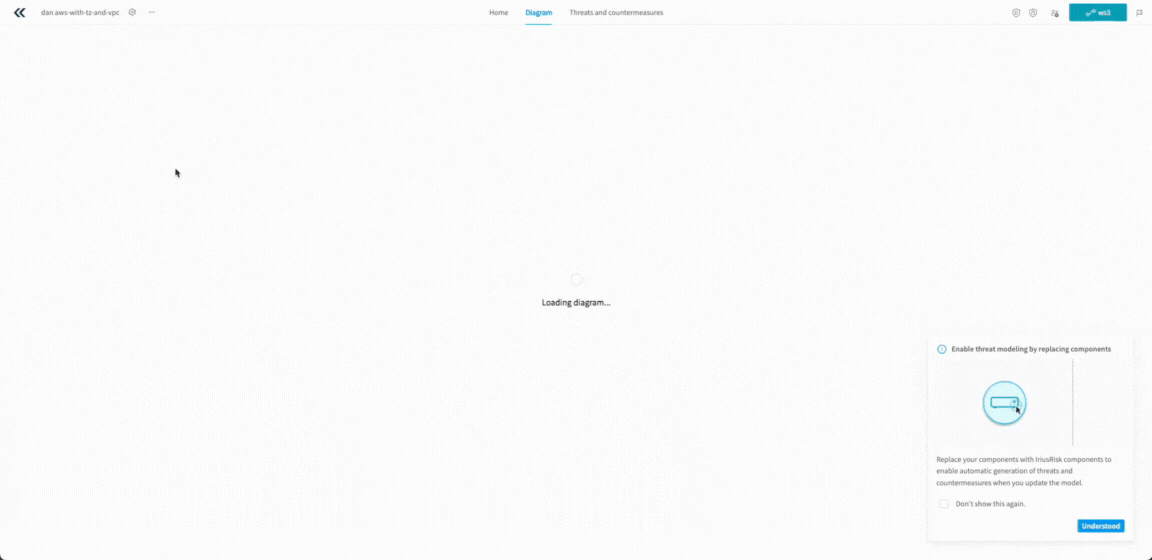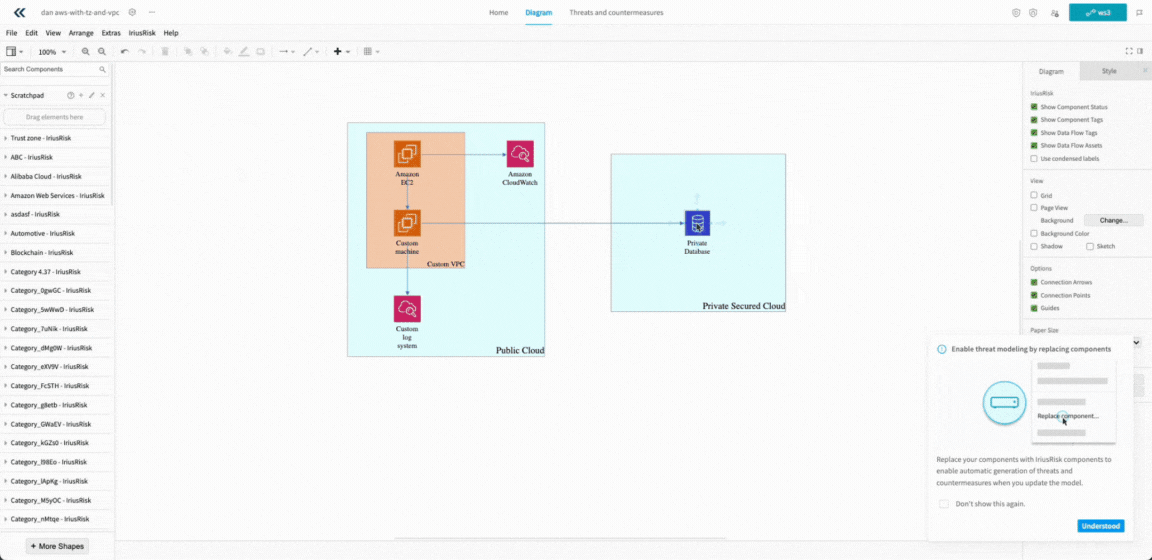
Improvements when Importing Visio and Lucidchart Diagrams
Imported diagrams from Visio and Lucidchart now retain their original layout, styles, shapes, colours, and other visual elements. This ensures your designs appear exactly as intended, maintaining consistency and accuracy throughout your threat modeling workflow.
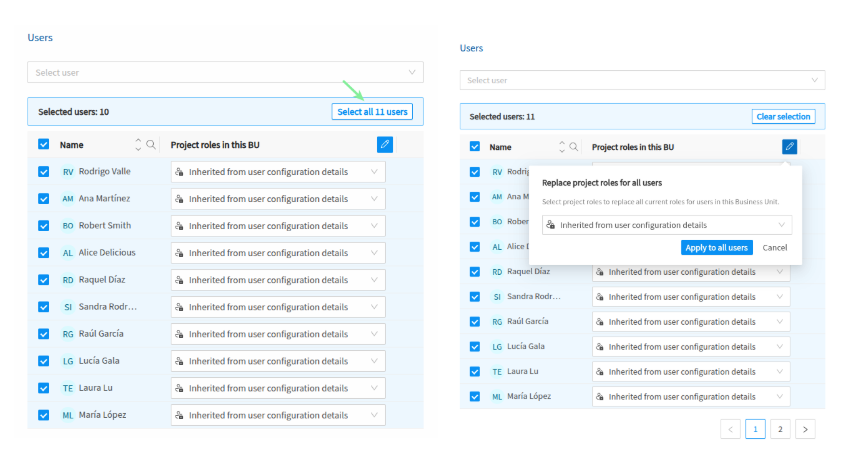
Bulk Permission Management for Business Units' Users
Managing project roles for large teams is now faster and easier. From the Business Unit view, you can assign or update permissions for multiple users at once—streamlining access management and reducing the manual effort previously required.
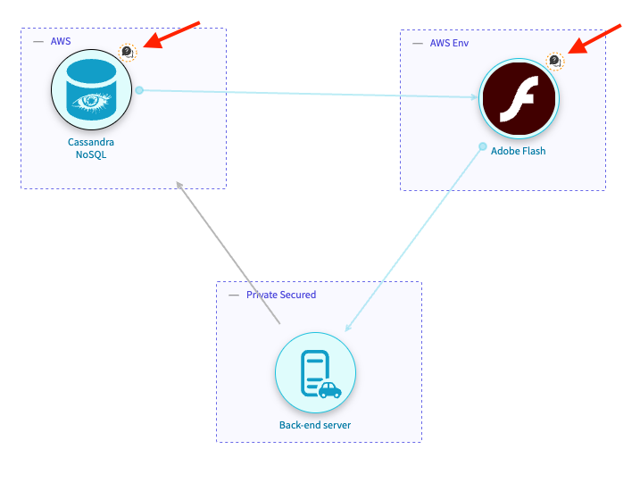
Spotting Unanswered Questionnaires to Improve Threat Modelling Accuracy
In addition to a Questionnaire section under Alerts that offers a clear, easy-to-find list of all components with unanswered questionnaires, once the model is synced, starting with release 4.45, components with unanswered questionnaires will also be highlighted in the diagram, as shown in the image below:
Additional Continuous Improvements
The ones are small but mighty! Take a look at what else we have been working on:
Enhanced Threat Exploration and Countermeasure Filtering
We’ve optimized performance so expanding and collapsing threats for components and use cases is now near‑instant, and filtering countermeasures for selected threats loads significantly faster, letting you navigate and refine your models with minimal delay.
Accurate Font Weights for Improved Visual Hierarchy
We’ve fully hosted the complete typeface so all font weights now render correctly, restoring the intended visual hierarchy, making it easier to scan pages and distinguish primary actions from supporting information for a more consistent, usable interface.
Inline Rename for Custom Field Groups
The edit action to rename custom field groups is now embedded directly within each group’s name, making it faster to find and update group names and streamlining your workflow.
Dropdown Search Discoverability Tooltip
We’ve added a hover‑activated tooltip on dropdown menus to let you know you can type to search, improving awareness of this feature and streamlining how you find and select options.
Improved Vulnerability Tracker Notifications
We’ve enhanced both the success confirmation and connection‑test error messages for vulnerability trackers, after saving you’ll see a clear acknowledgment that your tracker is ready to use, and if a test connection fails you’ll receive guidance on checking your settings or connection, so you always know the status and next steps.
Clarified Invitation Error in Community Edition
When you invite a colleague whose email is already tied to an existing Community account, the inline error now reads “A user with this email already exists,” clearly indicating they’re already signed up and can simply request login access.
Security Content & Standards
Fixed component name: A2A Protocol (Agent-To-Agent)
Fixed CIA risk rating on all threats in V2 libraries
Release Notes and Documentation
For more information, see Version 4.45 Release Notes or check out our Documentation.
Shape the future of Threat Modeling with us!
Join IriusRisk Horizon - Customer Research, Product Discovery, and Early Access. Join today.
Swaggerhub & Github
Find out more of what you need in GitHub and Swaggerhub Repos:
https://app.swaggerhub.com/apis/continuumsecurity/IriusRisk/1.24.0 - We provided this featured API to allow for deeper customer integrations as well as enable very flexible automations within the many varied environments IriusRisk needs to operate.
https://iriusrisk.github.io/iriusrisk-api/v2/latest/- Please note that this version of the API is currently in beta. While it offers advanced features for deeper integrations and flexible automations, we reserve the right to make breaking changes during this phase and encourage caution in production environments.
https://github.com/iriusrisk/IriusRisk-Central - Provides content useful for IriusRisk threat modelling, including templates, API scripts, libraries and more.


