.png)
Product Release 4.29: Featuring Improved Speed & Ease of Use
Overview
IriusRisk 4.29 includes major enhancements and improvements:
- Get simplified threat model output with our drastically improved Threats and countermeasures view
- Easier editing of content with brand new interfaces for risk patterns libraries and rules
- Improved accuracy and actionable countermeasures with refreshed v2 components
- Plus a ton more! This is our biggest release yet
Before we get started…
Welcome to our latest product release, packed with significant enhancements designed to streamline and improve your threat modeling experience. But they all work together, along with the improvements we have released over the past few months, to give you some key benefits that will take your threat modeling to the next level.
These benefits include:
- Improved efficiency through streamlined interfaces that reduce time spent on threat modeling tasks
- Enhanced threat model accuracy through better prioritization and reduced noise in the threat model output
- User-friendly experience with intuitive design, navigation, and improved in-product guidance that makes the platform easier to use
- Greater flexibility thanks to the expanded capabilities and integration options that offer more ways to customize and automate your threat modeling
Get simplified threat model output with our drastically improved Threats and countermeasures view
One of the biggest and most impactful changes in this release is our shiny new Threats and countermeasures view, which fundamentally changes the way you interact with threats and countermeasures for the better. Highlights of this view include:
- A single view that combines both threats and countermeasures
- A big focus on the countermeasures - after all they’re the things you’re going to implement to improve the security of your applications
- Powerful yet simple navigation of the threats and countermeasures
- A cleaner interface that’s easy on the eyes and intuitive to use
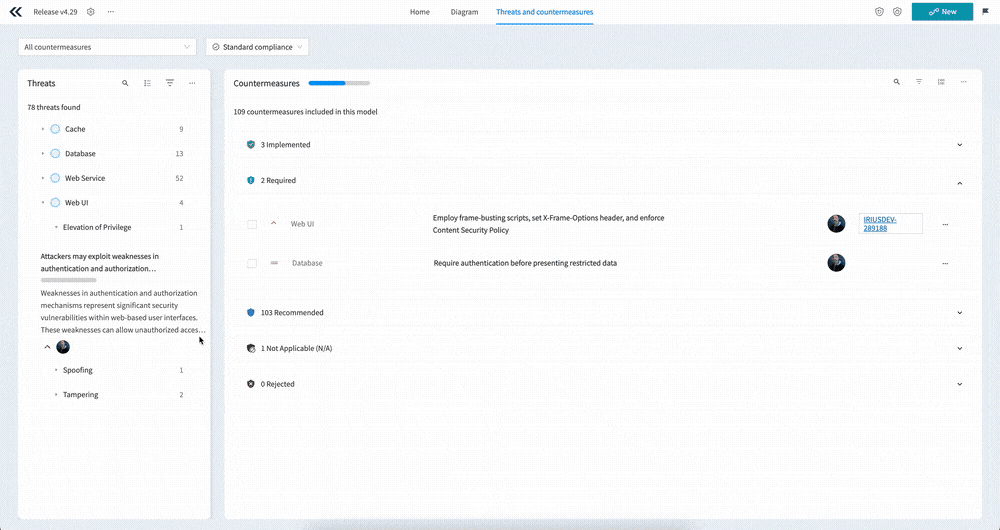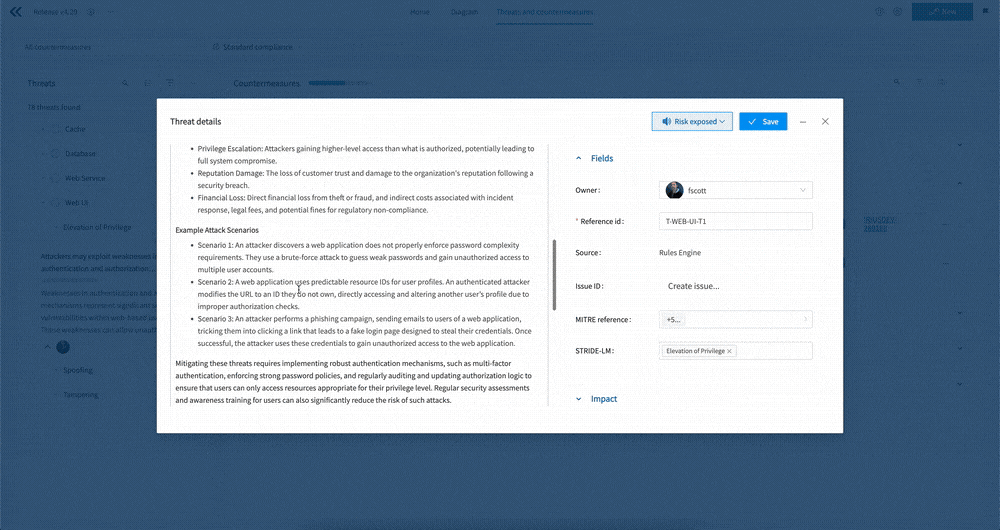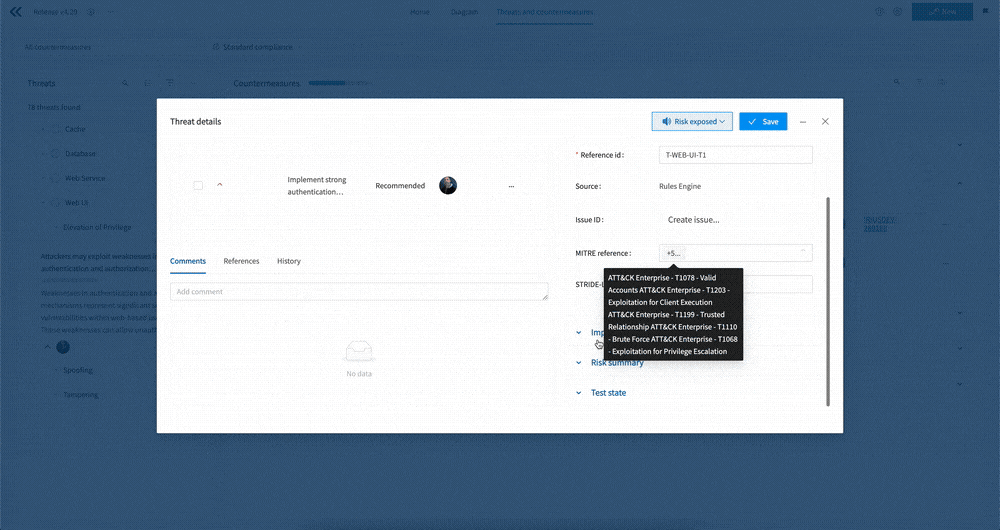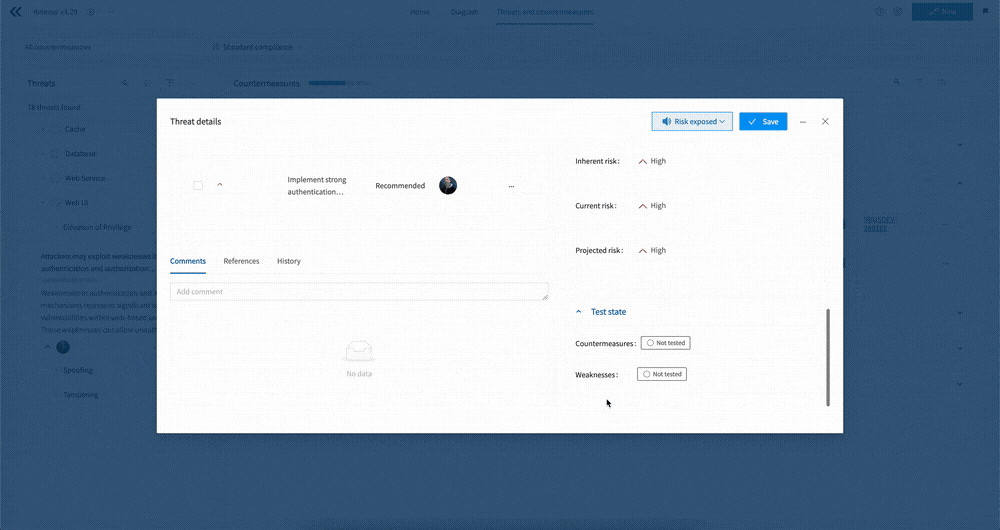
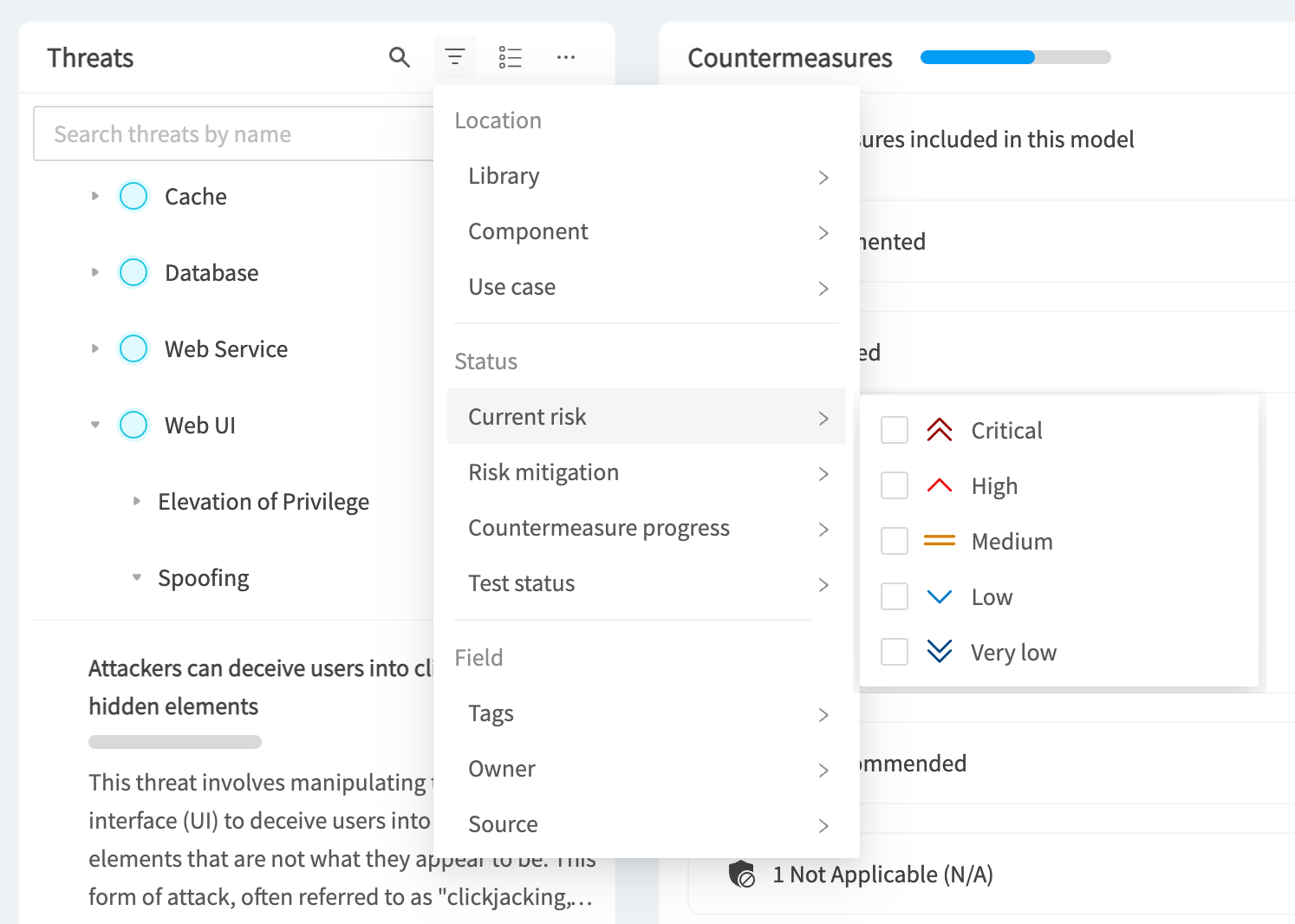
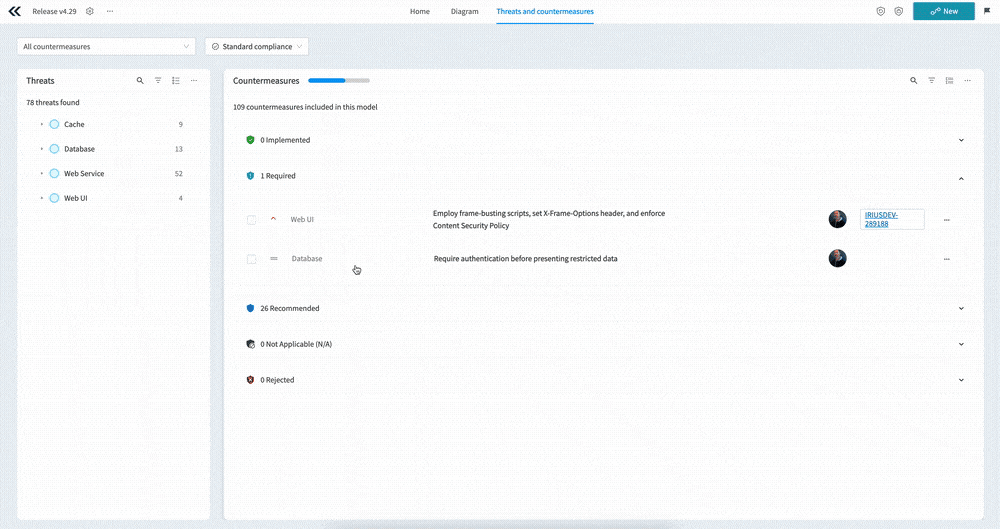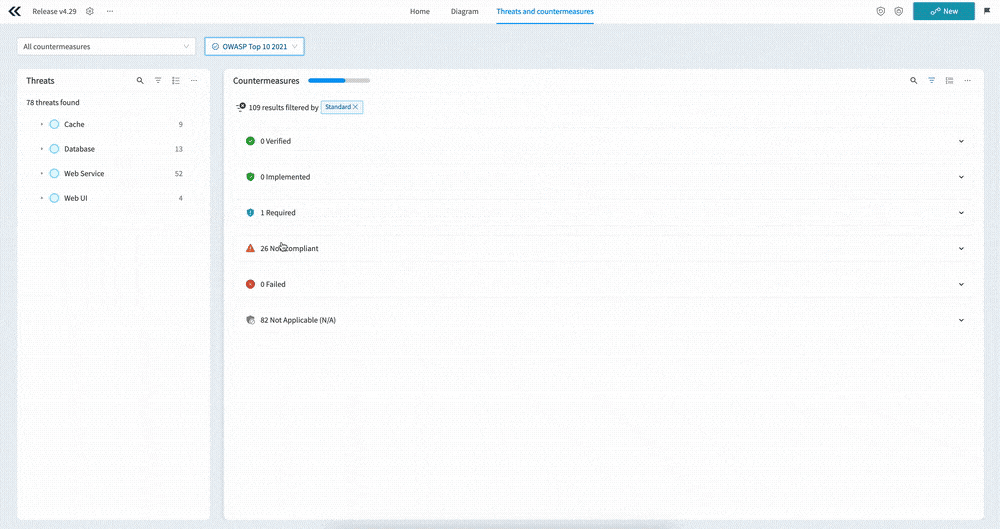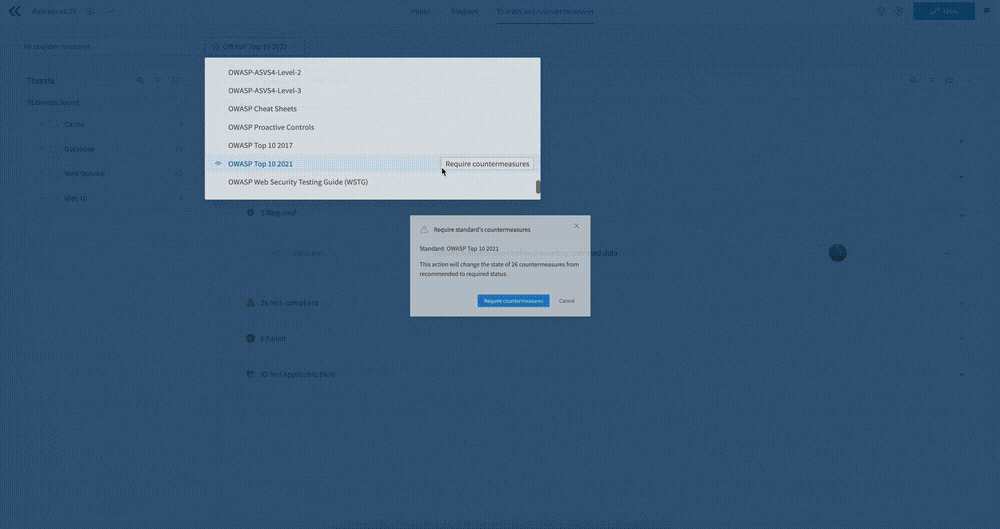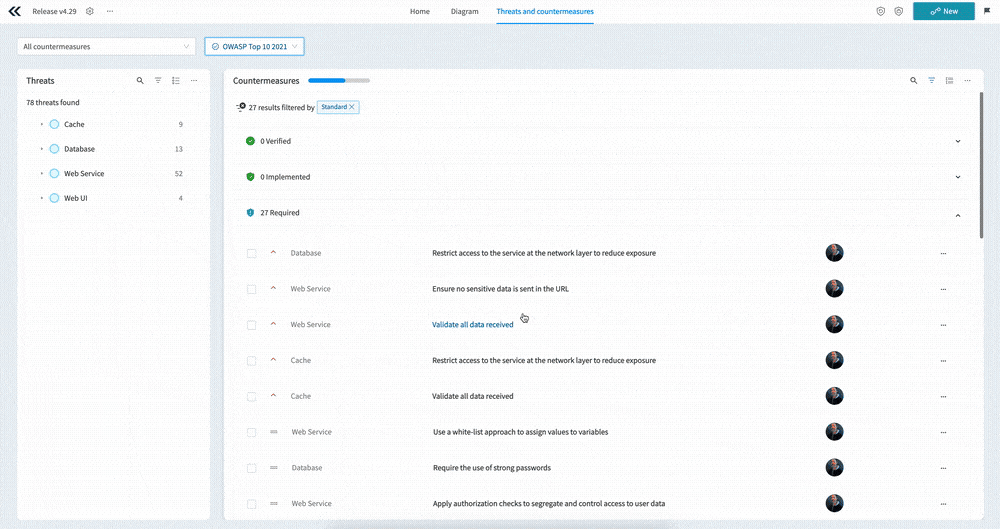
Interface overview
Before we go into detail about how you use the new interface, it makes sense to take a brief look at the main interface elements on the screen.

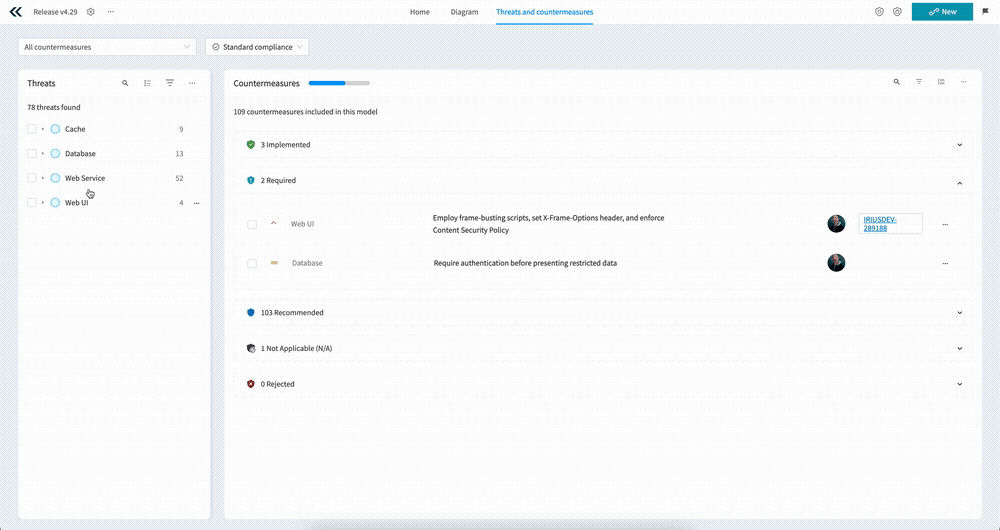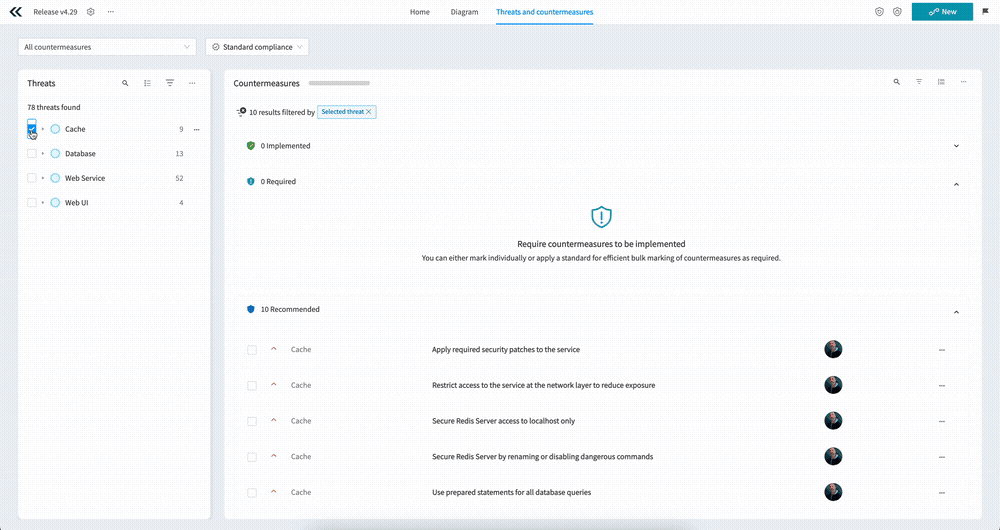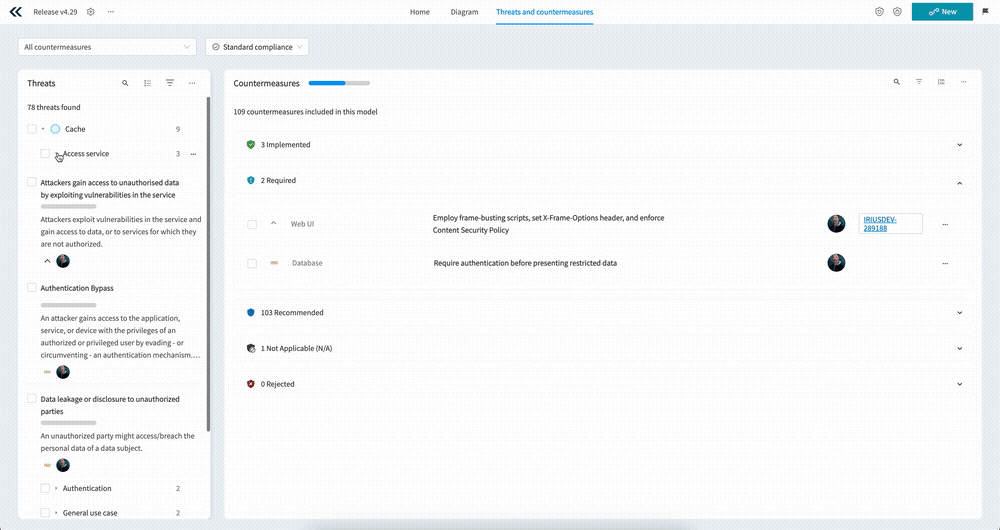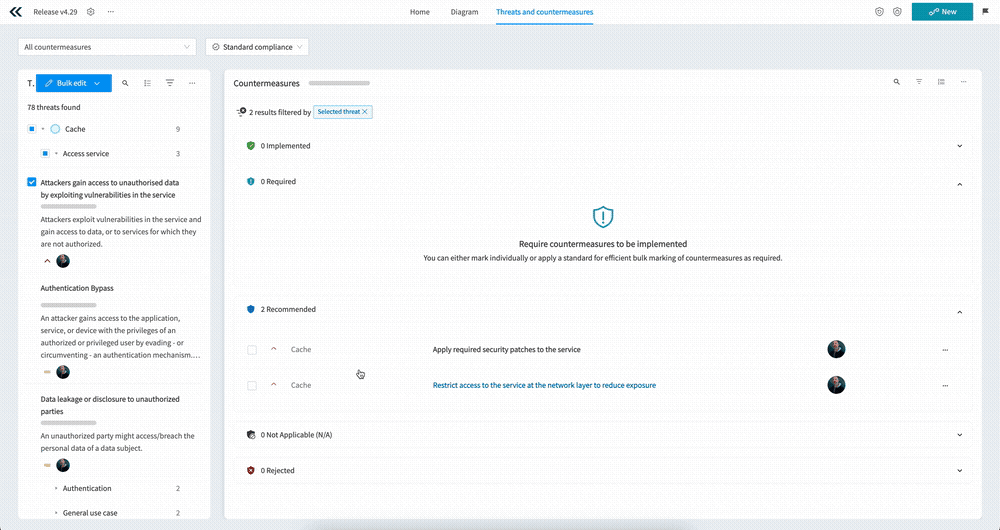
Looking at the screenshot above, you’ll see the following main sections:
- A - Custom Views which allow you to select from pre-defined countermeasure filters
- B - Standard compliance - filter the countermeasures by the select Standard, or mark relevant countermeasures as required
- C - The main Threats menu allowing you to search, filter, and take bulk actions on threats
- D - The nested list of components, use cases, and threats
- E - Countermeasure progress, showing you how many countermeasures are implemented vs required
- F - The Countermeasures menu, allowing you to search, filter, group, and take bulk actions on countermeasures
- G - The countermeasures themselves
Countermeasure grouping
The first thing you’ll notice when looking at the countermeasures is that they are grouped by implementation status and that the Required section is expanded by default. This means you have instant access to the countermeasures you have to act on.
You can change the grouping from the countermeasures menu.

Countermeasure details
Clicking on a countermeasure opens it up in a modal, giving you access to all of the information associated with the countermeasure. This includes the Name, Issue reference, Priority, Description, Fields, Standard References, as well as Comments etc.
For our new v2 components you’ll notice the inclusion of new MITRE reference and Scope fields, so check out the section on the v2 components before for more information.

Countermeasure actions
To the right of the countermeasures you find three ellipses. Clicking these opens up the actions menu for the countermeasure and allows you to set the Status for the countermeasure or delete it.

Countermeasure progress
The countermeasure progress bar at the top of the screen is a simple but effective indicator on how you’re progressing on the implementation of required countermeasures.

Countermeasure search, filters, and bulk actions
The Countermeasures menu at the top right gives you access to everything you need to further refine your view of the countermeasures. This includes:
- Search bar to search by specific key words
- Filters such as by status, priority, or Issue ID
- You can change how the countermeasures are grouped here as well
- And the three ellipses allow you to carry out bulk actions as well as other actions such as creating new countermeasures
Navigating countermeasures by components, use cases, and threats
By default you are shown all of the countermeasures in the threat model, grouped by implementation status, unless you have a Custom View that changes that. The main way of navigating the countermeasures is using the Threats view on the left.
Selecting a Component, Use case, or Threat automatically filters all of the countermeasures by the the selected element. This means you can quickly “zoom in” on countermeasures that are relevant to the task at hand. And of course, you can select multiple Components, Use cases, or Threats if needed.
Threat details
The Threats view also gives you access to threats themselves, which is useful if you want to know more about the “why” of a countermeasure. To view a specific threat, just click on the three ellipses next to the threat name and select “Threat details”. This will open up a modal showing you the threat, including then Name, Risk, Description, Fields, and Comments etc.
Threat actions
The threat menu also allows you to take other actions on the selected threat, such as changing the status or adding countermeasures.

Threat search and filters
Use the menu at the top of the Threats view to search threats, filter by location, status, and fields, as well as carry out bulk actions.
Flattened threat view
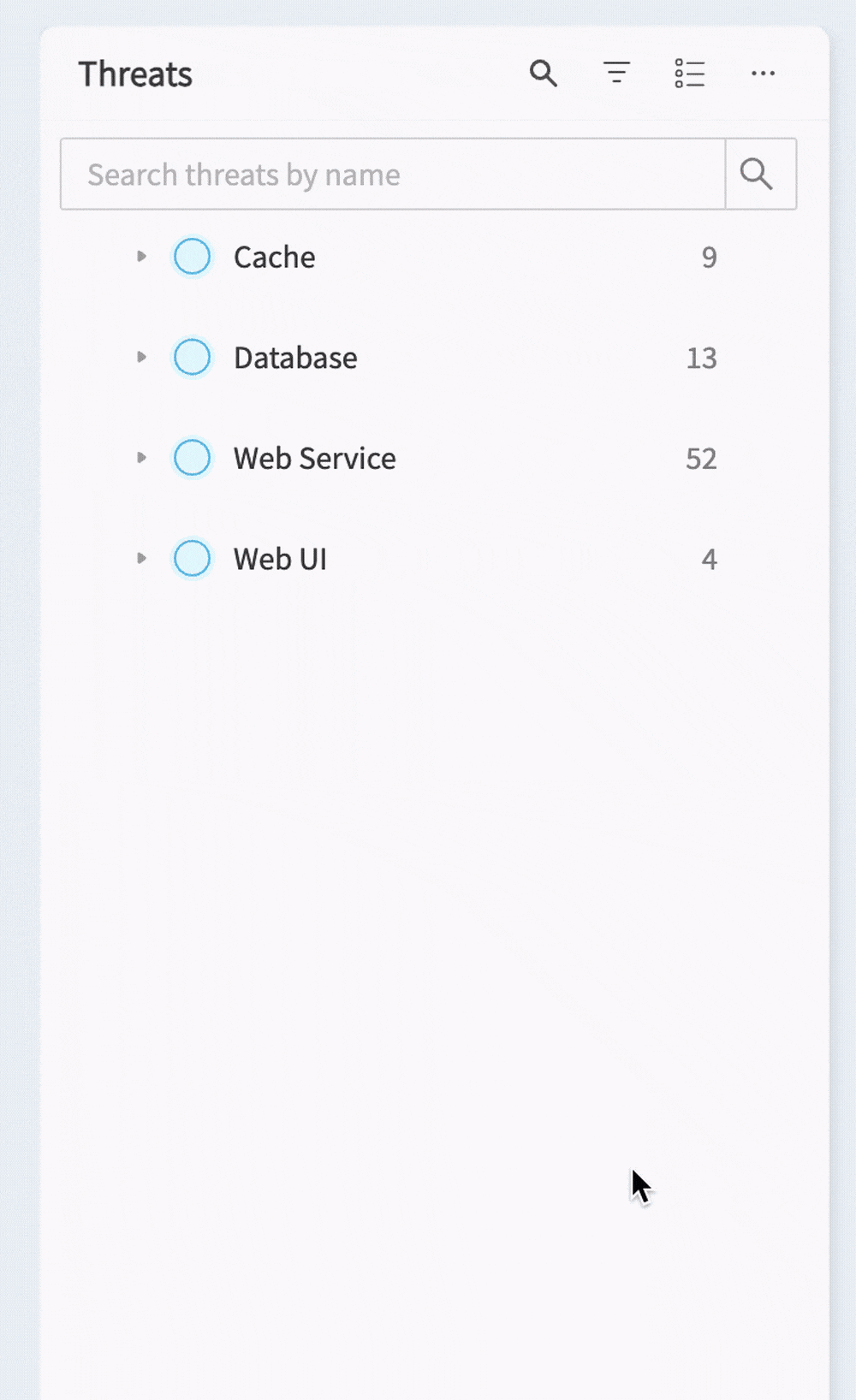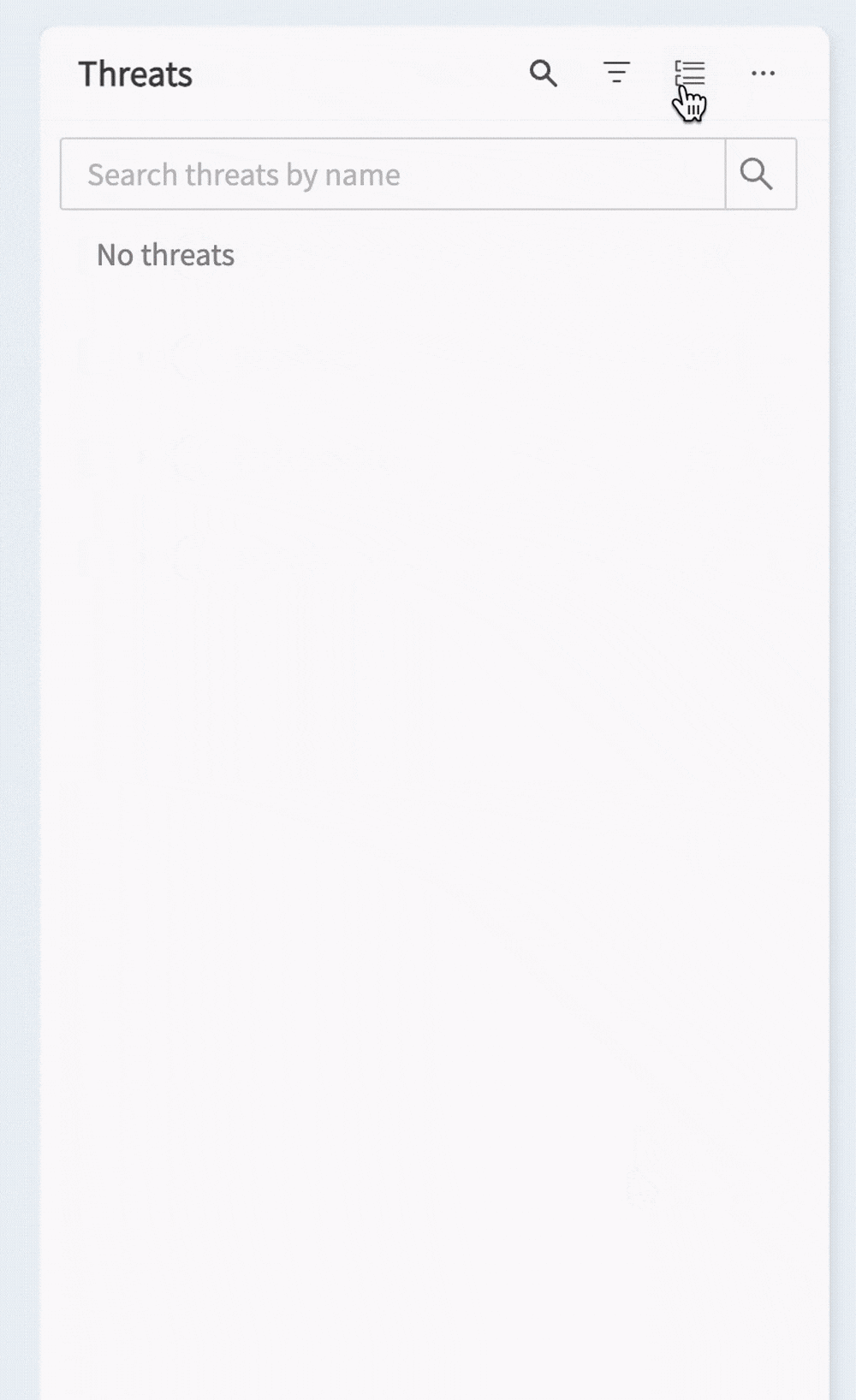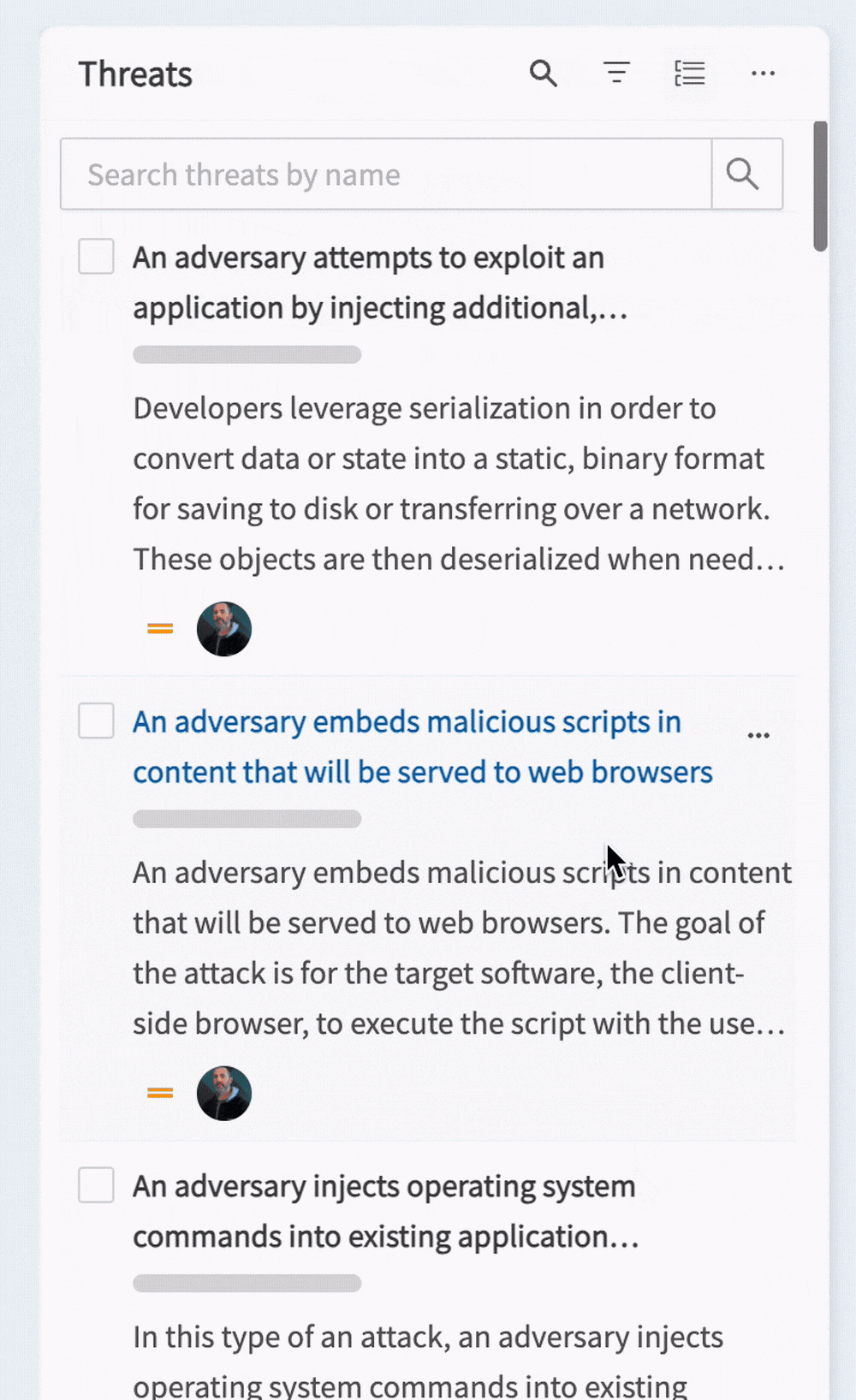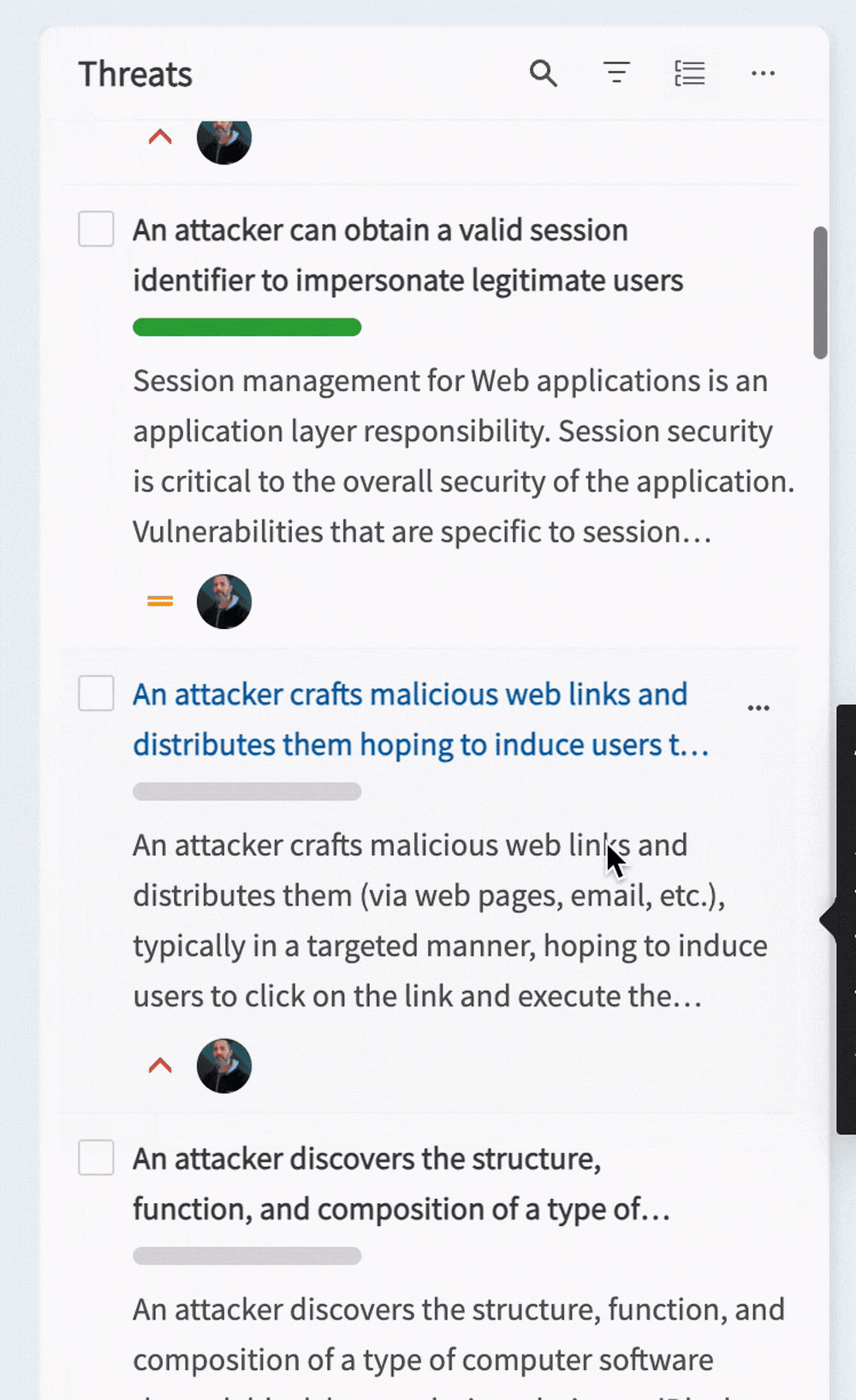
In the Threats menu you’ll also see a button that lets you toggle between the default Component Grouping view and a Flattened view that gives you a flat list of all of the threats in the threat model.
Custom views
Custom views can be selected from the dropdown at the top left of the page. These allow you to create predefined filters on the countermeasures, helping you to focus on the things that matter to you.
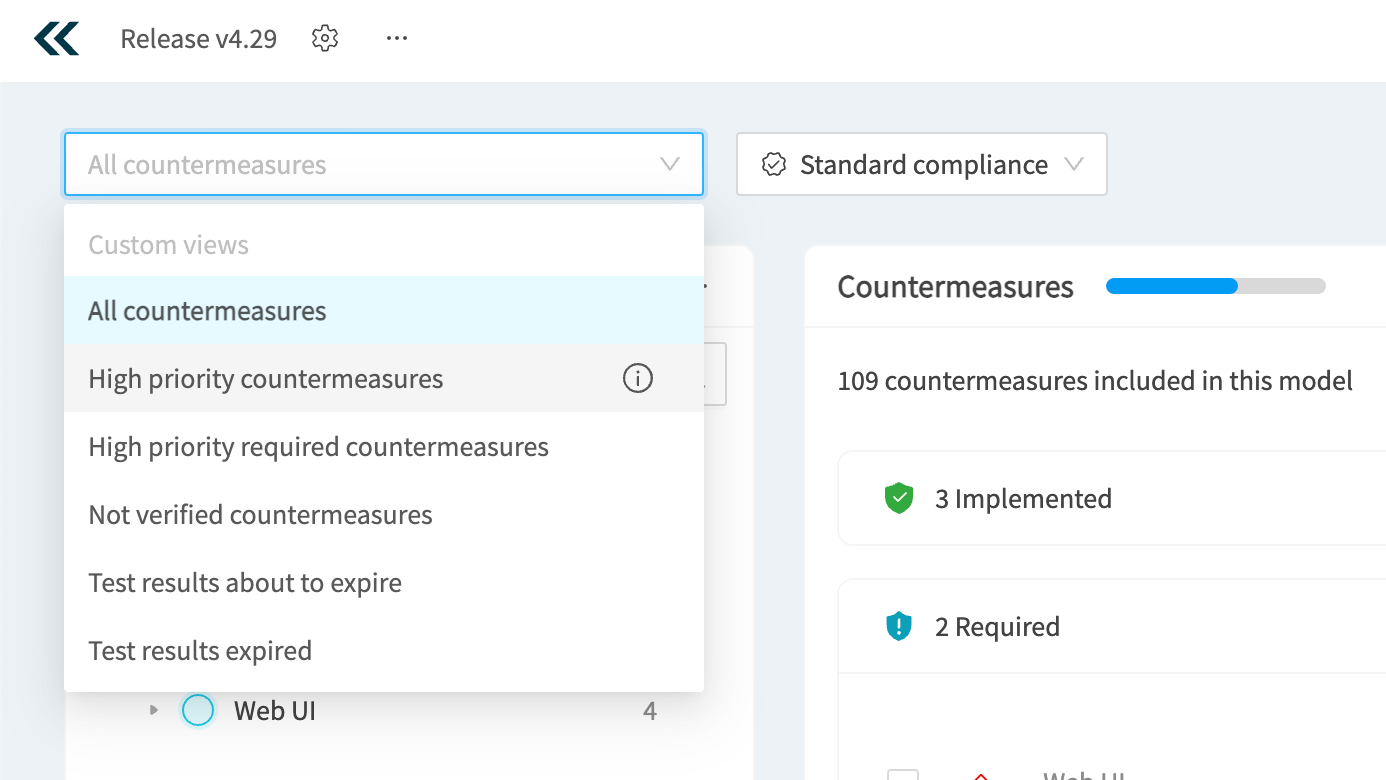
Standard compliance
The Standard compliance dropdown allows you to group the countermeasures by the selected standard. This is especially important if you want to understand the state of compliance of your application relative to a standard such as PCI-DSS. You’ll see which countermeasures are implemented, which are required, and which are non-compliant.
You can also use this menu to automatically require the countermeasures in the standard. Clicking the “Require countermeasures” button will prompt you to mark all of the relevant countermeasures as required.
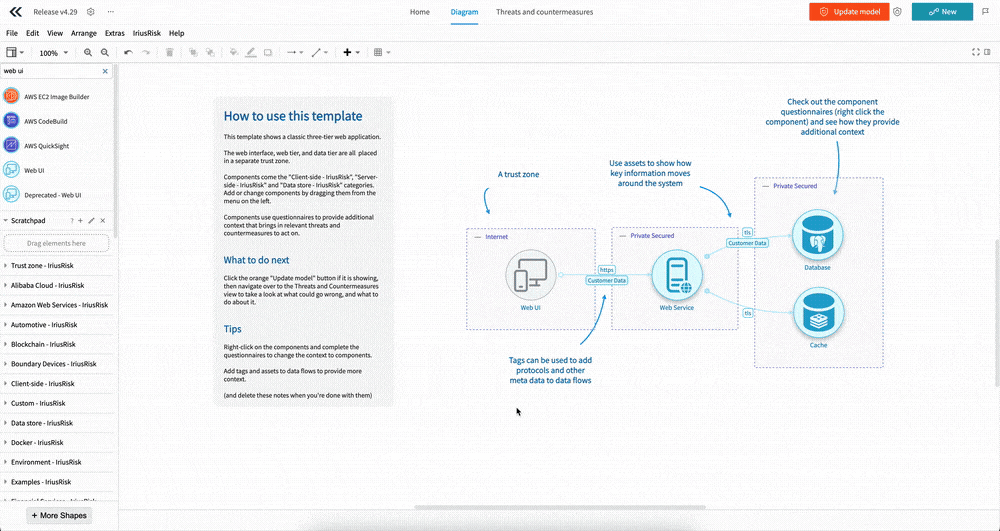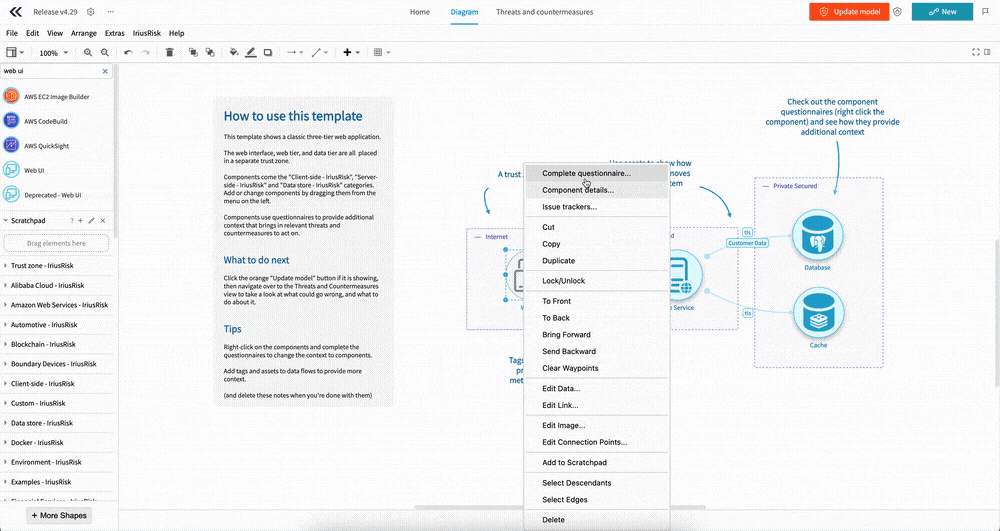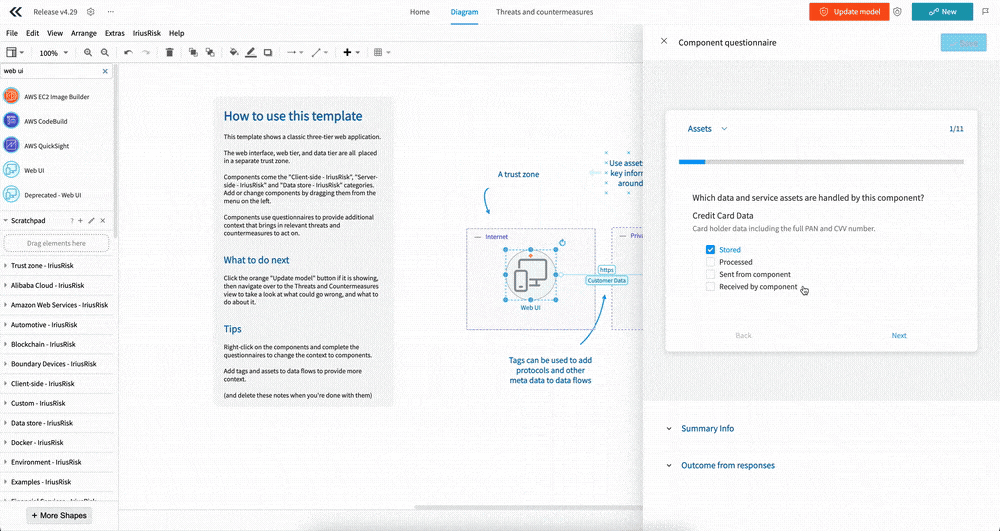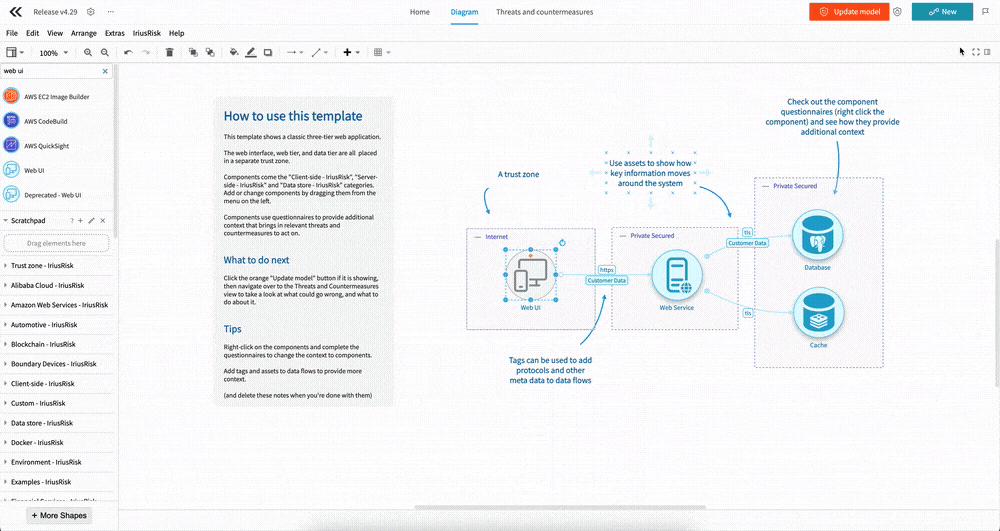
Intuitively complete Questionnaires to enhance your threat models
This release improves how questionnaires are shown and completed, making the experience much more streamlined. It applies to both the architecture/model questionnaires and the component questionnaires, but we’ll focus on the component questionnaires here.
Opening up the questionnaires, such as right clicking on a component, opens up a panel on the right.
You’re immediately shown the first question, including a clear description and answer options, and you can quickly navigate between questions using the “Next” and “Back” buttons.
A progress bar and counter shows you your progress and will be green when you reach the last question.
You can quickly jump between different question sections using the dropdown menu above the question.
To commit the changes, simply click the “Save” button at the top right.
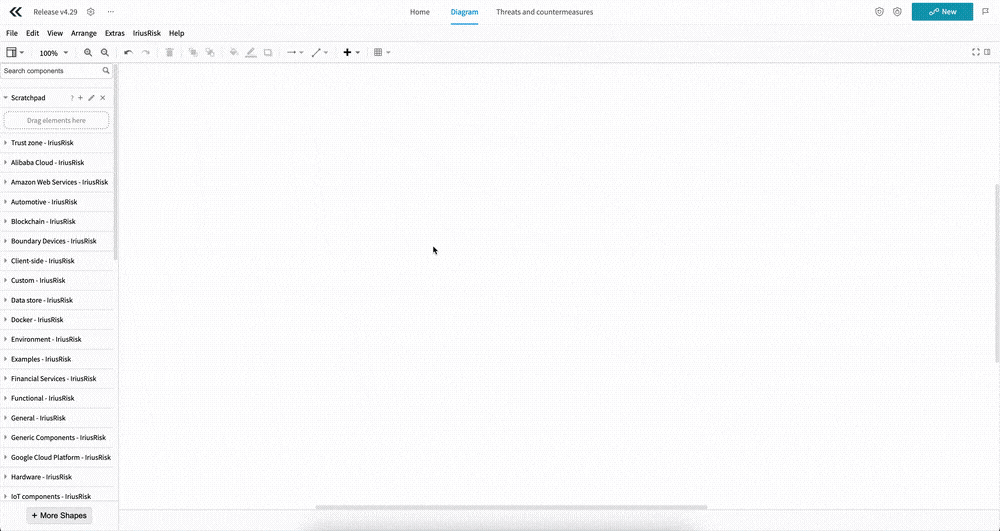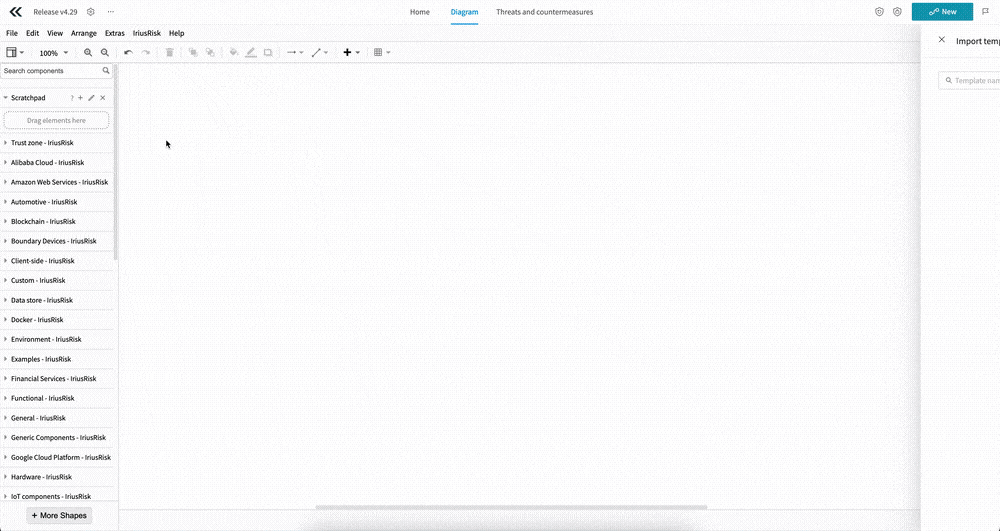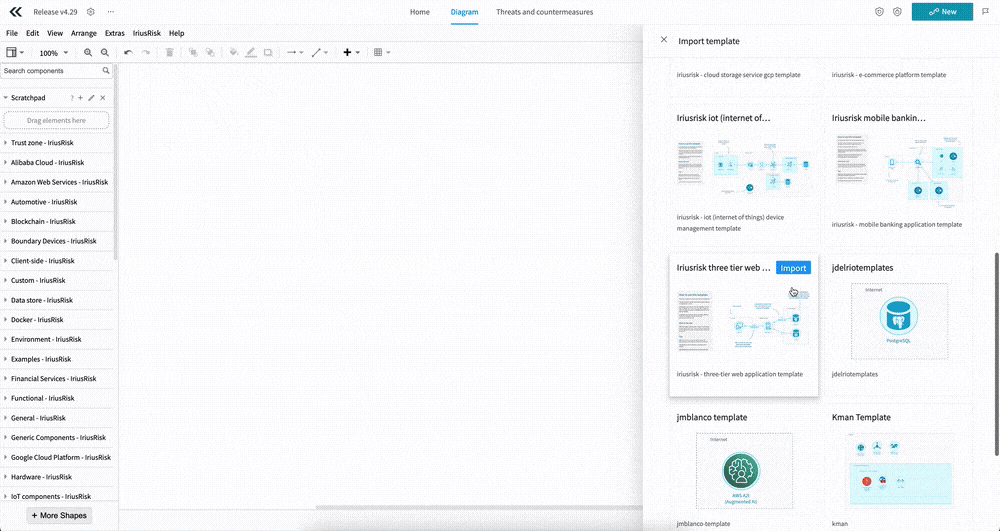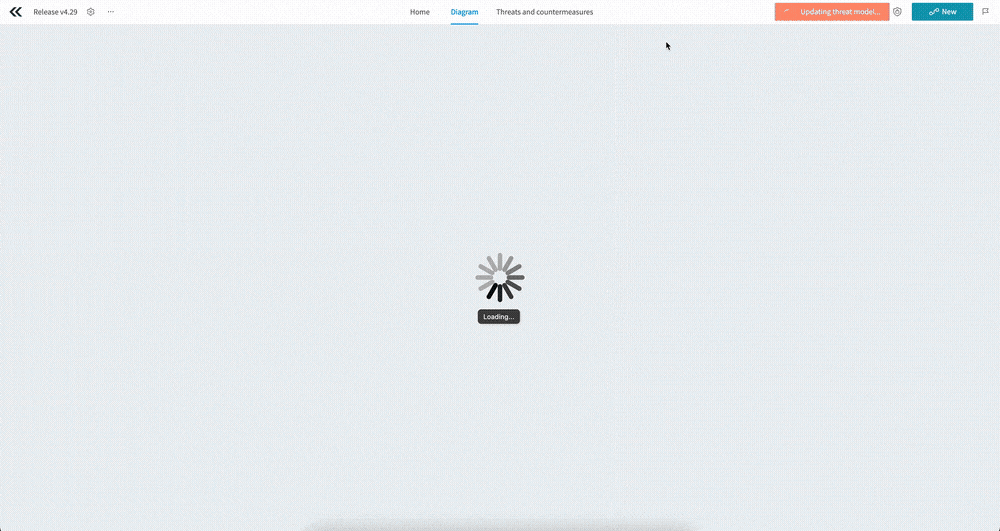
Learn from examples with a much improved Template import UI
Templates are a powerful feature that makes getting started with threat modeling easier, but getting you away from a blank canvas and giving you a starting point to work from. And importing templates just got easier with our new interface.
If you’re already in a project, you can open up the templates from the IriusRisk menu in the diagram tool bar. This will open up a panel on the right. Here you’ll see the list of templates with names, descriptions, and very handy diagram previews that let you get a sense of what the templates look like. To select one click the “Import” button for the template. You can also search templates and change the sorting.
Improved accuracy and actionable countermeasures with refreshed V2 components
Not only have we made an incredible number of interface improvements leading up to and including this release, but in this release we have also included the first batch of our new V2 components. These new components are a complete refresh, built from the ground up, and bring with them some key content improvements:
- Significant noise reduction in the output of threats and countermeasures
- Scoping output - “I only want to see what is relevant to my role”
- Improved prioritization - “show me what I should work on FIRST”
- Robust standardized framework for mapping countermeasures: full traceability -” I want to know how and why IriusRisk has mapped X to Y”
As well as:
- STRIDE - “I understand STRIDE, my colleagues understand STRIDE” - now IriusRisk does too
- MITRE ATT&CK - “We use MITRE as our internal language across DevSecOps and our SOC”
- Questionnaires - they now reduce the output of threat models rather than increase it
New vs deprecated components
As we’re basically starting from scratch with these components, we’re taking the opportunity to adjust them as we go. This means some components may be removed, others replaced, or merged, or just improved as is.
Don’t worry, we haven’t removed the old components and your existing threat models won’t be affected. As we replace components, the old ones are moved to a “Deprecated” category and are there if you still need them.
In v4.29 we have included over 60 new components, including:
- API Endpoint
- 3rd Party API Service
- Web Server
- Login and Logout
- Relational Database Management System (RDBMS)
- Plus many more
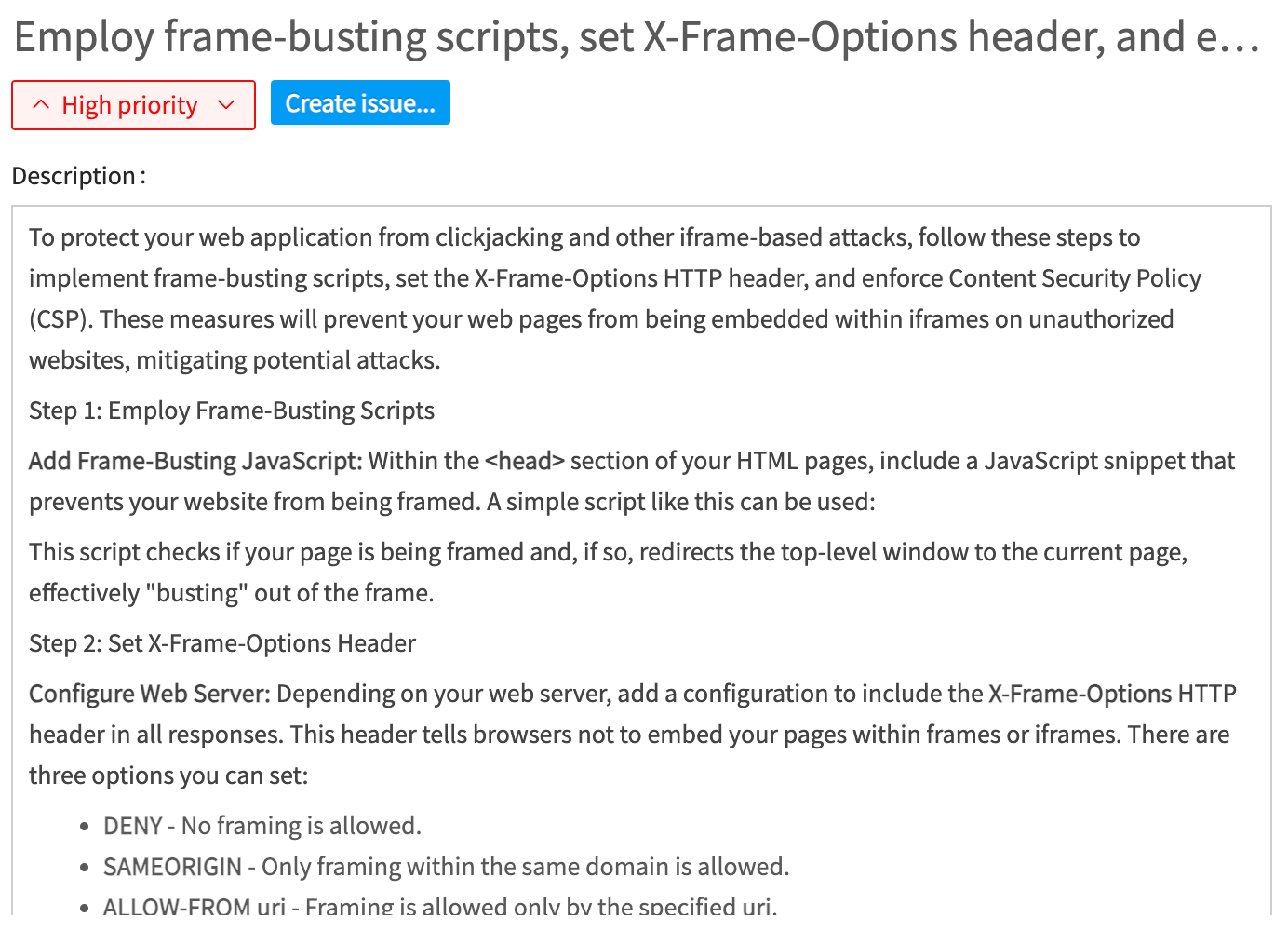
Developer friendly and actionable language
The threat and countermeasure descriptions have been re-written, with language aimed and developers and security experts alike, with many countermeasures merged into a single more descriptive countermeasure.
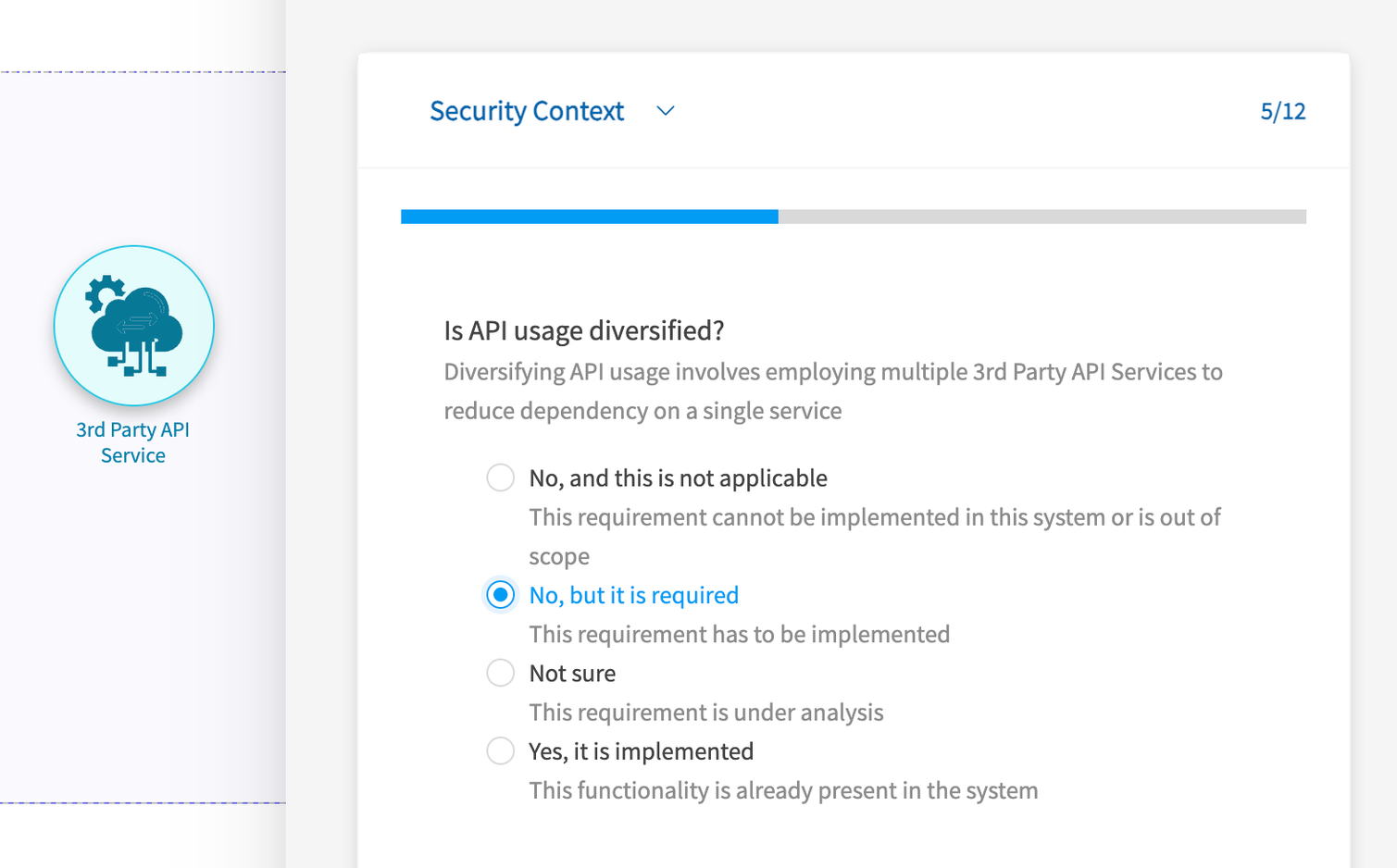
Intelligent component questionnaires that do the threat modeling for you
The component questionnaires included in V2 components are designed to do a lot of the heavy lifting of threat modeling for you.
By simply answering a few questions as you create your diagram, you automatically reduce the threat model output. How? Well, depending on your answers countermeasures can automatically be set to Implemented, Required, or Not Applicable. This saves time in having to review the countermeasures once the model is built.
Powerful threat and countermeasure metadata
The V2 components also include enhanced metadata on the threats and countermeasures that helps you put your threat models into context and focus on the actions that matter most.
For threats we have included the following fields:
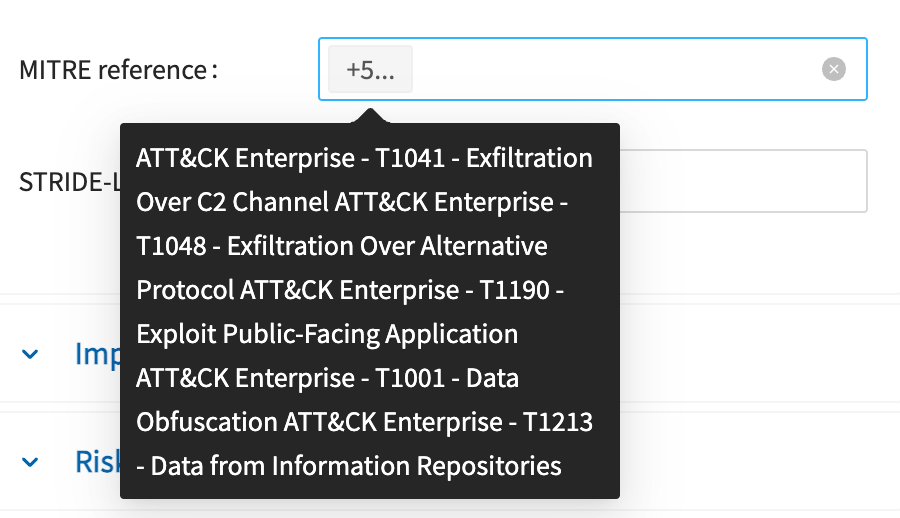
- MITRE reference - A threat can be associated with one or more MITRE framework attacks, such as from ATT&CK for many threats, or ATLAS for AI related threats
- STRIDE-LM - Threats have a reference to one of the STRIDE-LM categories, which stands for Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege, and Lateral Movement. The Use Cases that the threat sits under are also STRIDE-LM
For countermeasures we have included:
- MITRE reference - Countermeasures can be associated with one or more MITRE framework mitigations.
- Scope - This classifies the countermeasure based on security domain, such as Application security or Data security. This means that developers can focus on Application security controls, whilst DevOps focuses on other types like cloud and networking.
- Standard baseline - Countermeasures are mapped to standards, and the baseline provides the core entry point into that mapping. See the section below for details.
- Standard baseline section - This is the specific section in the baseline standard the countermeasure is mapped to.

Baseline standards provide consistency and transparency
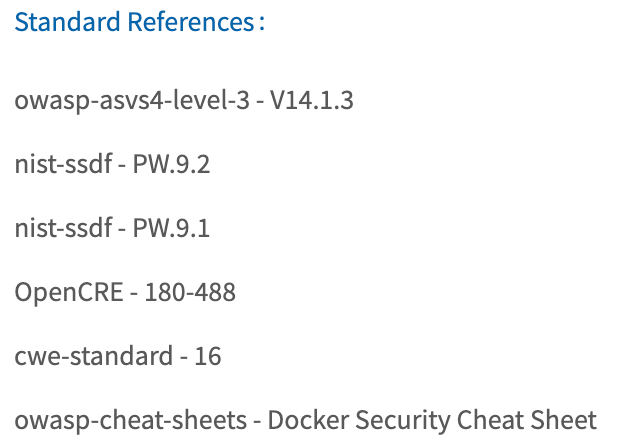
As described above, countermeasures are associated with a “Standard baseline” and a “Standard baseline section” field. IriusRisk uses the baseline and section to automatically propagate the countermeasure with other standard mappings.
For example, a baseline reference to ASVS V14.1.3 would mean that it is automatically mapped to the following standards:
Easier editing of content with a brand new interface for risk patterns libraries
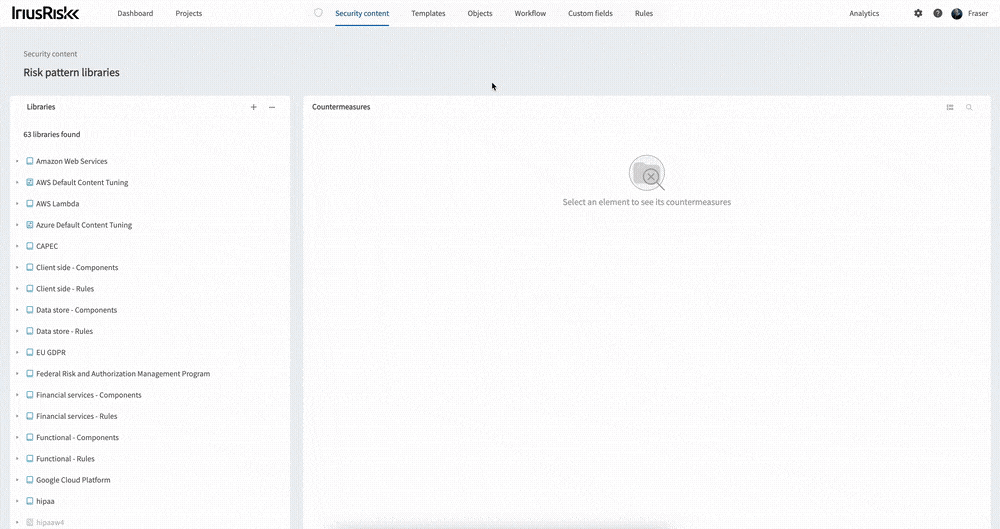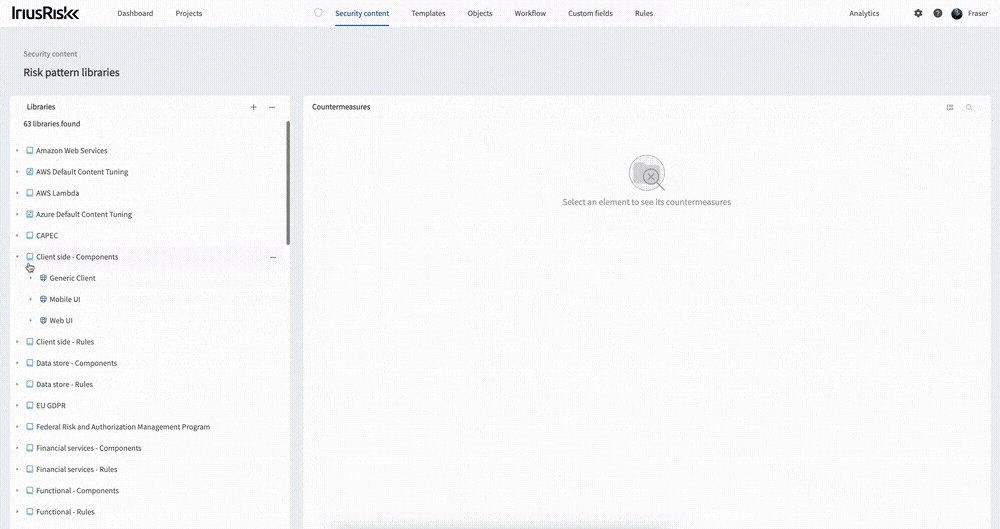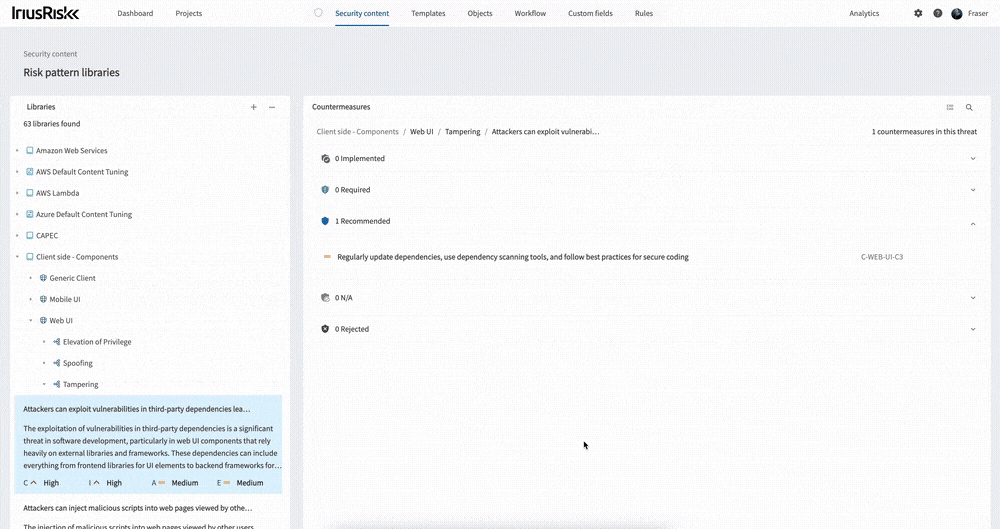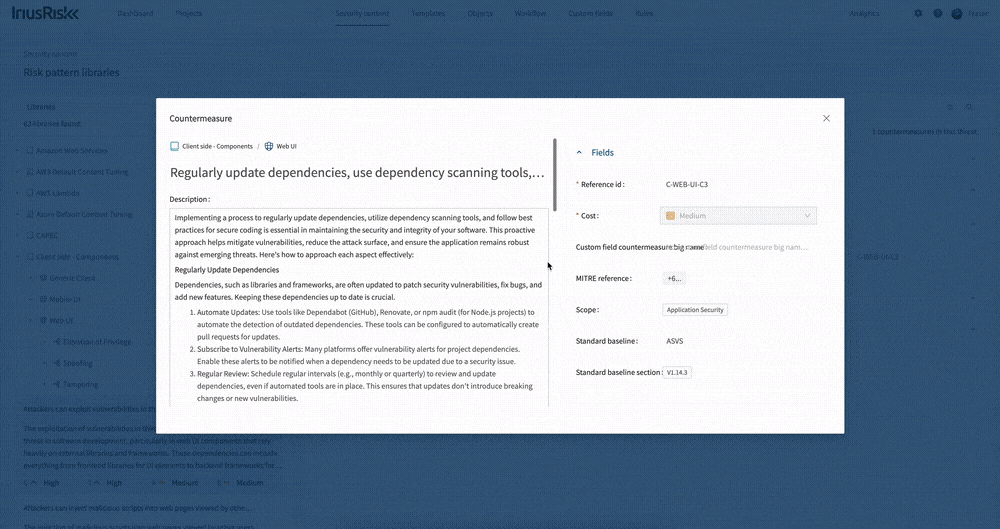
Release v4.29 includes an improved interface for viewing and managing risk pattern libraries.
Opening the interface up from the “Security content” menu you are presented with the list of menus on the left. Selecting one will load the countermeasures in that library. You can expand the libraries, components, and use cases to see the threats within the library. Selecting on any of these will filter the countermeasures by the selected item. From the Libraries menu you can create or import a library. Click the three ellipses next to an item such as a library or component to open up the menu for that item. From here you can add new risk patterns, use cases, and threats etc.
Manage hundreds of rules with ease using our new Rules interface
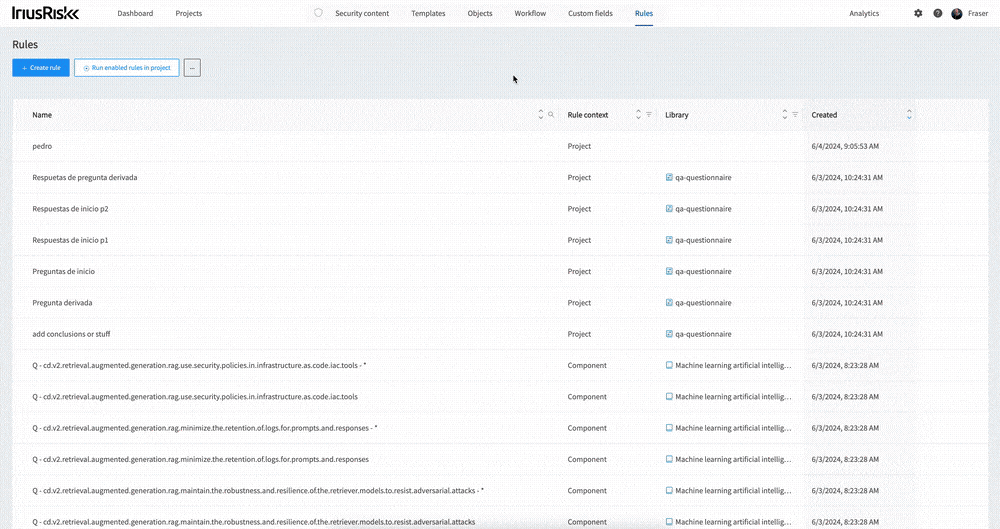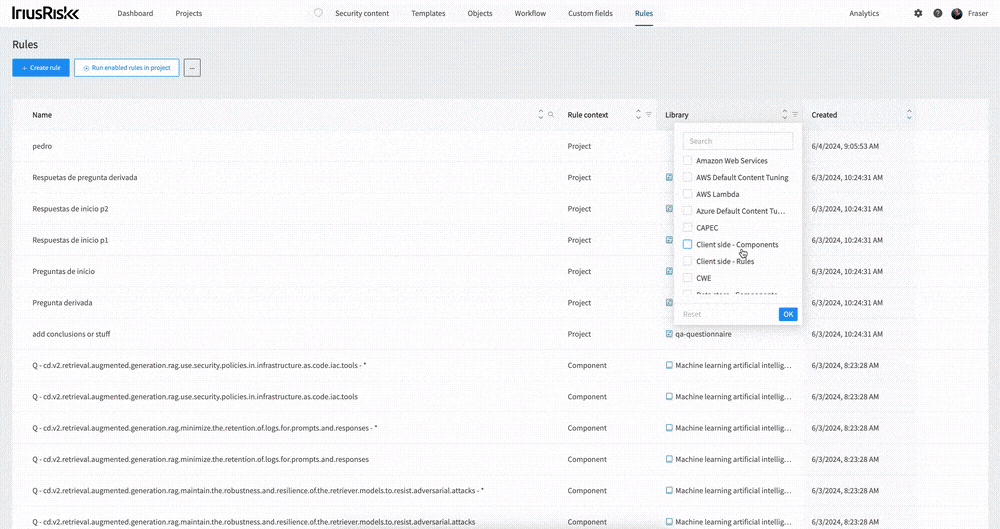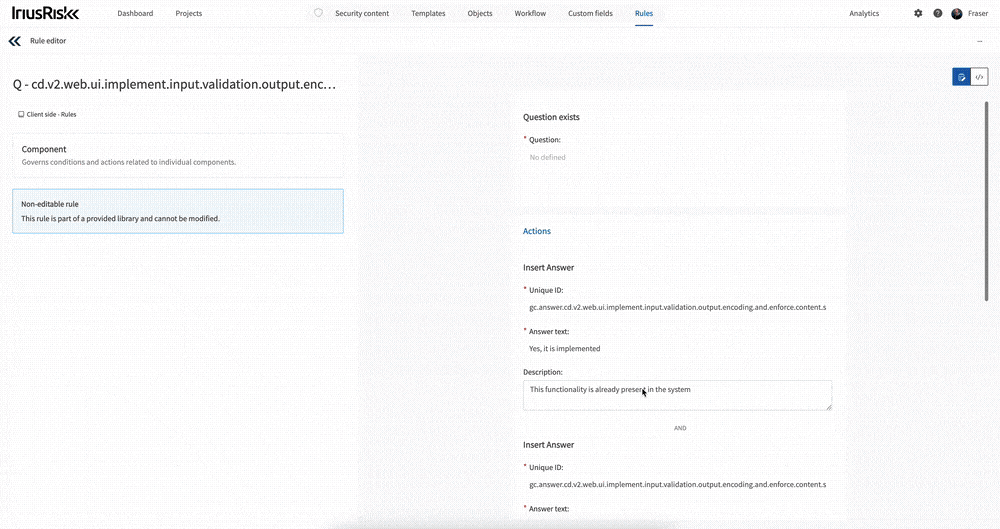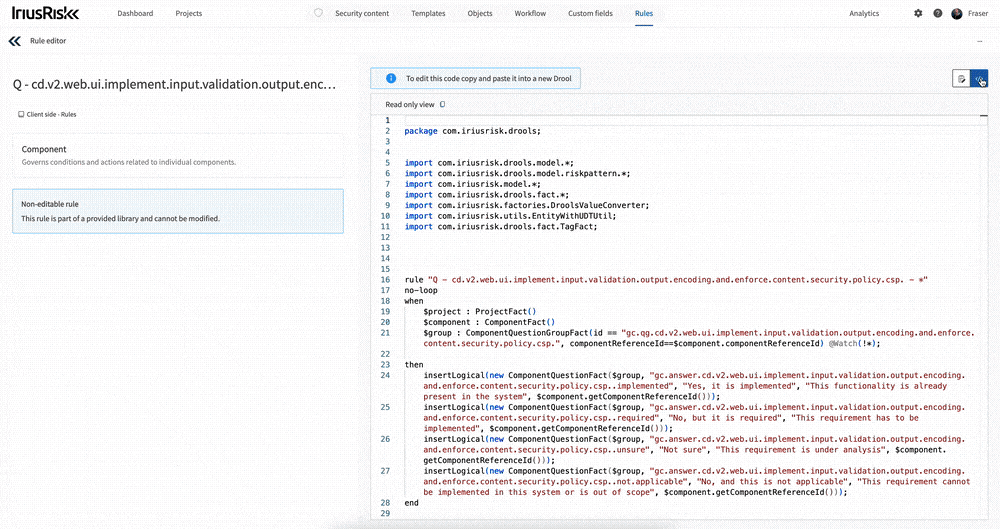
Rules are a powerful feature of IriusRisk that makes your threat models dynamic and contextual. Rules can do anything from importing new risk patterns based on a data flow, to changing countermeasure statuses based on tags. And with this update to IriusRisk, managing rules just got a whole lot more seamless.
Opening up the Rules interface from the top menu, you’ll be shown every rule in the system - so no more guessing which library a particular rule is in. From here you can search the rules by name, or filter them such as by rule context or library.
Clicking on a rule takes you to a new page. On the left you’ll see the library name and available options for the rule including the context, conditions and actions. On the right you’ll see a visual representation of the rule including the selected conditions and actions. To modify a rule just select the new condition or action in the left panel.
You can also switch to the code view of the rule using the toggle button at the top right.
Use your existing ABACUS architecture diagrams with a new OTM endpoint
Creating threat models from existing design artifacts is a great way to accelerate threat modeling and save time. In addition to support for formats such as Terraform, Cloudformation, Visio, LucidCharts, Draw.io, and the Microsoft Threat Modeling Tool, in this release we have included the beta version of our new ABACUS endpoint.
If you’re a user of the ABACUS architecture tool, you can now import those via the endpoint and create a threat model in IriusRisk automatically. For this beta release we have only included some basic component mapping, so if you want a more complete import you can customize the mapping file.

For more information on the new endpoint, check out the release notes here: https://app.swaggerhub.com/apis/iriusrisk/IriusRisk
User Enablement
Inspired by the big UI and UX improvements in this release, we have improved how users who are new to threat modeling and IriusRisk get started using the in-app guidance. We have introduced a new “Get Started” button that opens up a resource center containing short and focused videos on how to carry out the key tasks of creating and managing threat models.
This resource center replaces the previous approach of pop-ups with descriptions and animated GIFs.
The new videos include everything from creating a project to adding metadata, and from reviewing countermeasures to generating reports.
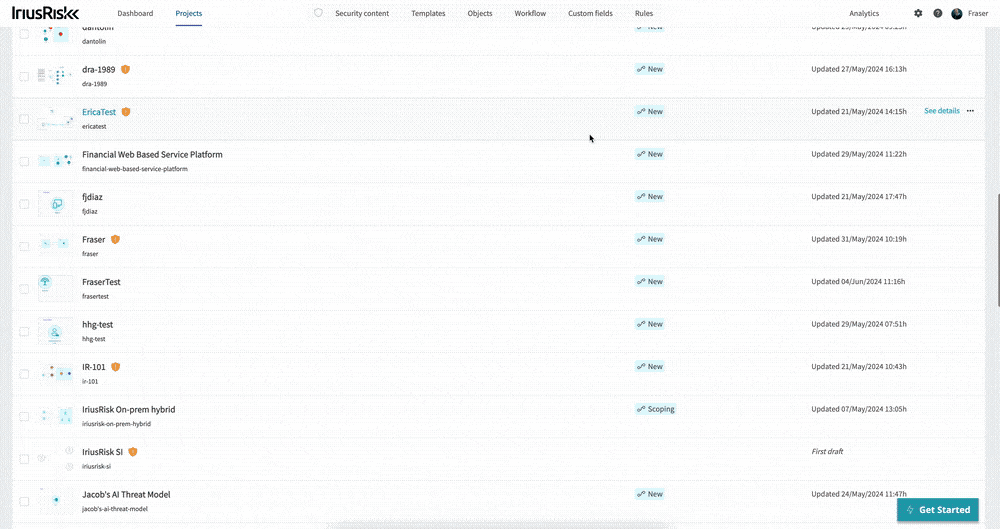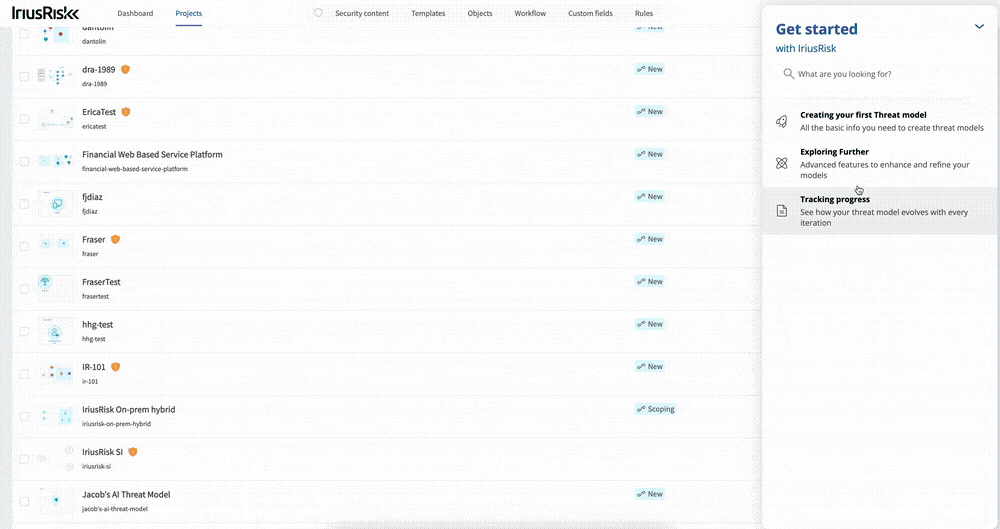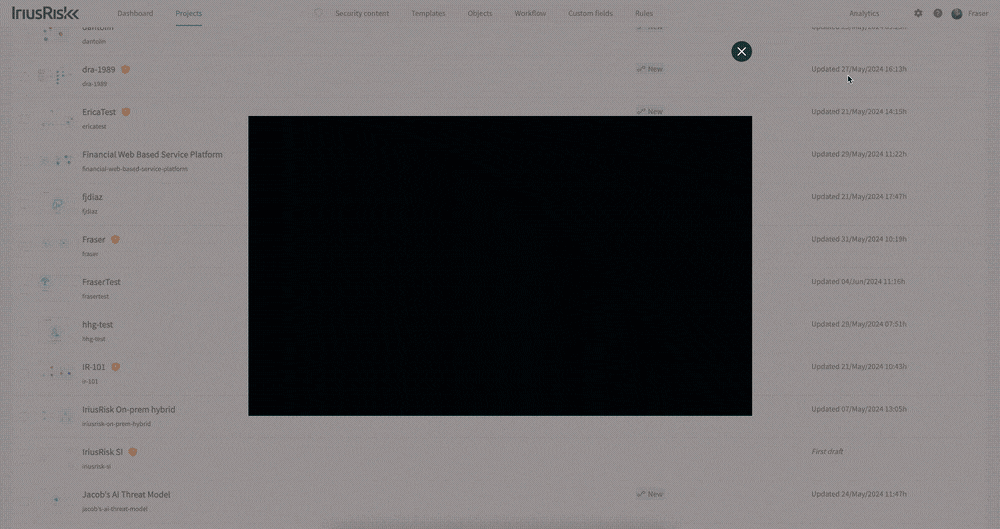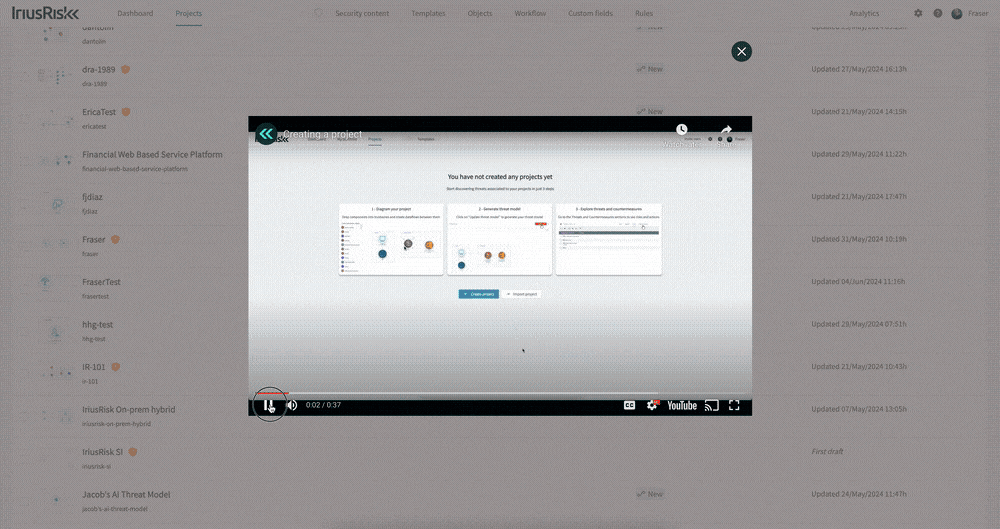
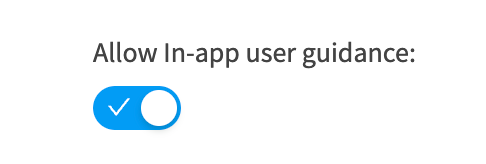
To turn on in-app user guidance, select the “User interface” option in the global settings menu and toggle the setting.
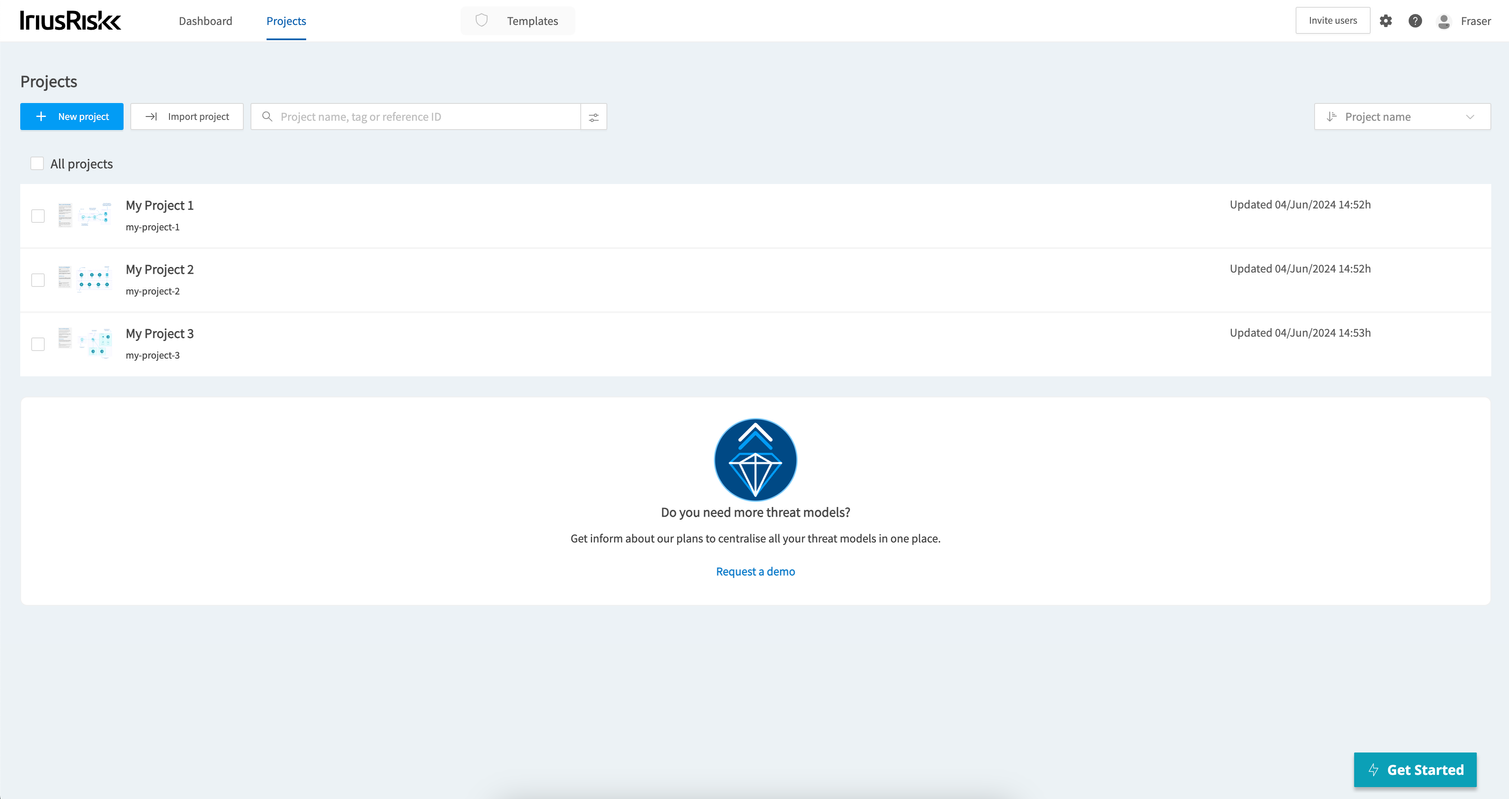
Community Edition users can now create 3 projects for free
Fantastic news for our Community Edition users! You can now create 3 projects for free in the Community Edition. This means you can threat model three different applications, or the same application from different perspectives - e.g. infrastructure versus business logic.
Other UI and UX improvements
This release also includes some other interface improvements. The Projects list navigation now scrolls below the fold and the dataflow details have been updated to match the Components details interface.
New API v2 endpoints
As of the end of our migration to React, we have released over 600 v2 API endpoints that you can use to automate and integrate IriusRisk into your SDLC and cybersecurity processes. The endpoints included in this release are:
- Projects
- Added bulk operations for updating and deleting countermeasures and threats
- Introduced endpoints for copying threats and weaknesses, and creating use cases
- Implemented retrieval of history and standard references for countermeasures
- Templates
- Added endpoints for creating, updating, copying, and deleting countermeasures and threats
- Introduced bulk operations for updating countermeasure priorities and threat states
- Implemented retrieval and management of standard references and history for countermeasures
- Libraries
- Added endpoints for managing countermeasure standard references, including creation, retrieval, updating, and deletion
- Introduced endpoints for copying and updating the state of countermeasures and threats
- Implemented summary and history retrieval for threats and countermeasures
What can you do with these new endpoints?
To give you an idea of what you could use these new components for, here some suggestions to get you started:
- Bulk update the status for a list of countermeasures based on a security analysis tool (e.g. SAST)
- Automatically pull the history for a countermeasure (or multiple ones iteratively) for audit purposes
- You basically now have all of the endpoints needed to manage libraries and content from code (something we’ve been working on for the V2 components and will be releasing later this year)
Deprecations
- My Portfolio - this section has been removed from the product
- Lock Threats - ability to “lock” threats has been removed
- “Risk” and “Limited” rules modules - rules context modules have been simplified and cleaned up
- “Allowed libraries to add and search for when adding Threats or Countermeasures” setting - not used, will be removed
- Importing automated test results - lack of usage of Micro Focus Fortify format import
- Editing “Test Results” source - lack of usage
- User Enablement - Existing spotlights and flows are being replaced by short embedded videos available through a “Getting started” beacon


